Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

It’s in the nature of security protocols to evolve and be replaced in line with the changing threat landscape. Discoveries of security flaws and vulnerabilities lead to protocols or their implementations updating regularly. We can see this in WPA or WEP and their variants evolving to WPA2 (Wireless Privacy Access II). Today, we are examining what the latest move to WPA3 means.
WPA and the Wi-Fi Alliance
WPA2 is now more than 10 years old, would you believe that? It replaced WPA in 2004. In real life, however, the various technology components did not become available to the mainstream until approximately two years later in 2006.
WPA3 was released in January 2018 by the Wi-Fi Alliance. This is a a non-profit organization that promotes Wi-Fi technology and certifies Wi-Fi products for conformity to certain standards of interoperability. It owns the Wi-Fi trademark and logo, which may only be used by manufacturers who have certified their products for compliance and interoperability in accordance with the certification program managed by the Alliance.
Since its inception in 1999 the Alliance has grown to more than 550 members, of which only 14 have the “sponsor” designation. These are global players who are typically trendsetters in the industry. They are: Apple, Comcast, Samsung, Sony, LG, Intel, Dell, Broadcom, Cisco, Qualcomm, Motorola, Microsoft, Texas Instruments and T-Mobile.
Before diving into some of the security benefits of the new standard, let’s take a look at some statistics related to the security protocols currently in use. These are sourced via Wigle.net who consolidate location and information of wireless networks worldwide to a central database. They have user-friendly desktop and web applications that can map, query and update databases via the web.
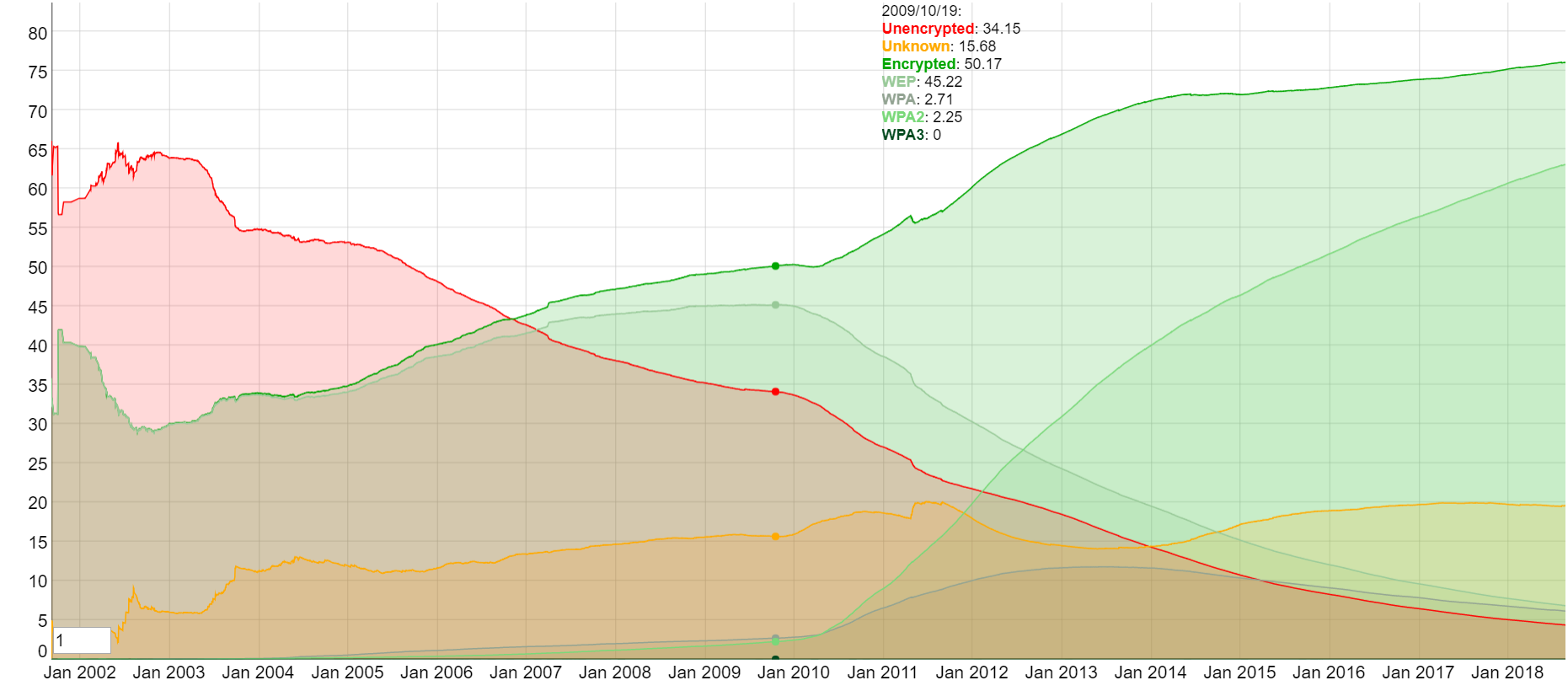
The clear trend from the above graphic is that unencrypted networks are clearly on the decline. We see a little over 4% in 2018 and there is about a 1/5 in an unknown state. This leaves 76% for all of the encrypted networks. WEP and WPA take 6% each while 63% uses WPA2 (all figures are rounded).
You could interpret the progress made since 2002 as good but not good enough. It leaves us questioning what the update of the new WPA3 standard will be? There are a lot of unknowns. It is a complex relationship with multiple parties involved. We see software and hardware vendors on one side while business and consumer users sit on the other.
Looking at the history of WEP, WPA and WPA2 in the context of flaws and vulnerabilities, the following highlights are worth mentioning:
Before getting into some technical details, let me briefly share a few of the security benefits of the new protocol:
Manufacturers are already getting new devices certified, but it will still take a few months. My guess is that we won’t see much on the market before the 2018 Christmas season. A wider adoption may follow by the second half of 2019.
The change to WPA3 will also put various vendors to the test. It will show whether they will invest in their brands by developing a security or firmware upgrade to support WPA3.
One thing remains, if you want faster speed and more reliable signal, it may be time to consider an upgrade anyway, especially with 802.11ax on the horizon.
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
I am the COO and Director of Professional Services at Advantio.
I have been at the forefront of the Payment Card Industry starting with PCI DSS version 1.0 in 2005. Since then I have executed hundreds of assessments, delivered numerous trainings and have been a keynote speaker at industry events across Europe, the Middle East, Asia, North America and Africa empowering organizations to defend themselves against modern-day cyberattacks.
Certifications: CISSP / CISA / PCI-QSA
Comments