Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

Historically cybersecurity has been regarded as a function of the IT department. Data is stored on computer systems, so the IT Director is made responsible for protecting it.
And it remains true that many of the security measures used to protect data are IT-based. Firewalls, permissions, encryption – all are technical solutions to the problem of preventing data loss, theft, and leakage.
In recognition of these superior security safeguards, cybercriminals are having to develop more advanced methods of attack. Bypassing perimeter firewalls is no longer enough to gain access to your network.
The unfortunate truth is that people represent the biggest risk to corporate security. Not hackers – your employees.
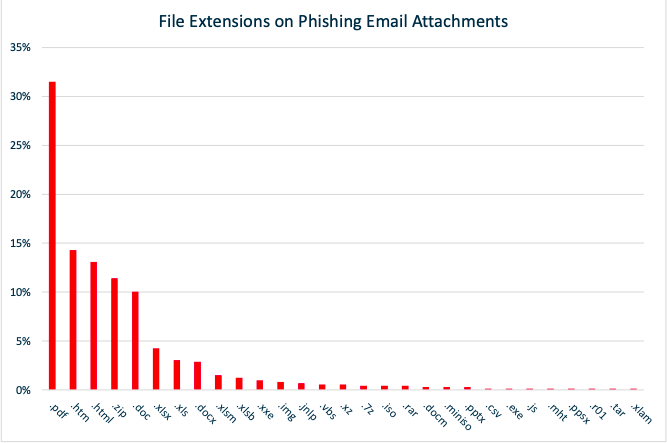
Despite increased awareness of the dangers of fraudulent emails, it remains the key point of entry for most cyber attacks. UK Government figures suggest that 72% of attacks in 2017 were launched via email.
Img. 2
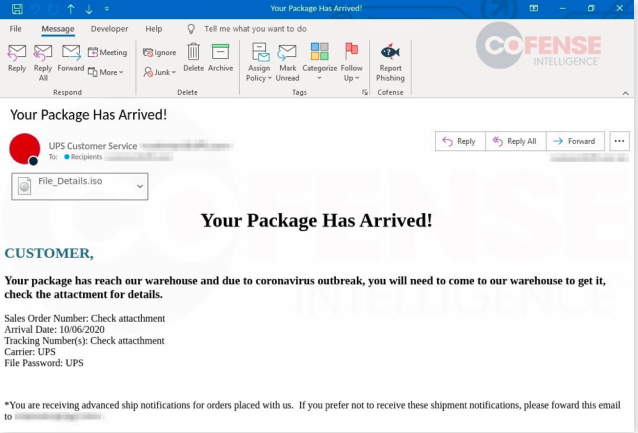
Again, perimeter defenses are very good at detecting and blocking malware and ransomware, but bad messages still get through sometimes. In most cases the malware lies dormant until someone opens the infected attachment, triggering the payload.
The same scenario is repeated with compromised webpages, infected removable drives, and insecure personal devices connected to the corporate network. The IT team will implement automated systems to minimize these risks – but the staff has a part to play too.
And this is where the importance of culture comes into play.
With so many potential attack points, the key to improving security is to create a culture of healthy suspicion. In the era of openness and social business, this approach may seem counterintuitive, but the stakes are too high to continue making basic mistakes with security.
Effective security culture will mean moving from the traditional “trust but verify” model, to a new “verify then trust” alternative. This means that any email, file, or approach by a third party should be considered hostile until employees prove otherwise.
The reality is that Advanced Persistent Threats (APT) use multiple vectors to compromise your security – including spoofing communications from trusted sources. Maintaining a healthy level of skepticism helps to reduce the risk of these more subtle techniques successfully infiltrating your systems.
Cultural change always starts at the top of the business. The IT Director may define what needs to change, but the rest of the C-Suite is responsible for communicating those changes to the rest of the business.
More than simply defining a vision, however, employees will need regular training. First, they need to be able to identify new attacks, and then ensure they continue to apply that knowledge.
Because people play an important role in starting or preventing APT attacks, it is critical that your people are properly prepared for their role in improving security. Data protection may not be an explicit aspect of most jobs, but everyone now has a part to play.
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
I am the Founder of Advantio.
Technology has been my passion since I was a kid; when I first heard the handshake of an old 300bps modem I realised security would be key in an interconnected world. Since then it has become my passion and primary focus.
The reason why I've started my own business is to make IT Security simple.
Certifications: CISSP / CCSA (Checkpoint) / ITIL Foundations / ACSA (ArcSight)/ Linux+/ PCI-QSA / PA-QSA
Comments