Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

NOTE: It is recommended that you read our previous article first: "DNS: The blind spot in the PCI DSS compliance strategy."
The almost omnipresent Active Directory is by far the most widely used identity management service in the world: over 95% of major companies use it on their networks, and despite or perhaps because of its great success, it continues to be a major focus of attacks today, and often due more to configuration deficiencies than unpatched vulnerabilities.
To summarize, the Active Directory service consists of a server with the role of "Domain Controller" whose main functions are:
As you can see, these features are critical, so if they were to be violated, many organizations would grant access to their main applications and databases to someone unauthorized.
The following is one of the main attacks from which we must protect ourselves, and which is usually the first step for more complex and critical attacks (SMB Relay, Pass the Hash, etc.).
By default, Windows systems use the following prioritized list of services to attempt to resolve name resolution request:
LLMNR (Link-Local Multicast Name Resolution), is a name resolution protocol over IPv4 and IPv6 that is enabled by default on Windows systems and uses the following connections:
On the other hand, NBNS/WINS (NetBIOS Name Service or also known as Windows Internet Name Service), is also an old name resolution protocol, in this case only over IPv4 and which uses the following connections:
LLMNR on comes in first and NBNS second, will come into play when for any circumstance DNS resolution fails for a request from a network resource that requires authentication, or directly when there is no DNS service for that network; when that happens, the flow is as follows:
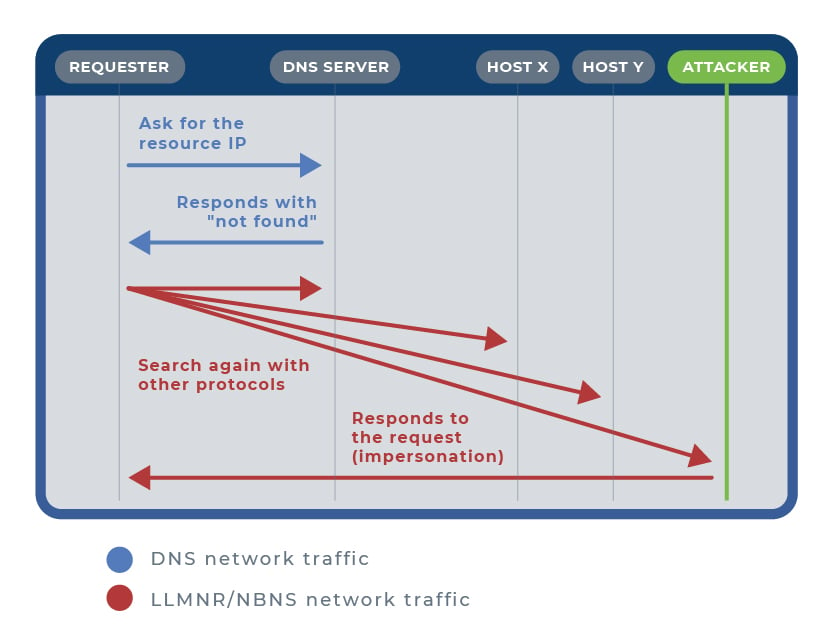 Exploiting LLMNR/NBNS
Exploiting LLMNR/NBNSA particular, well-known case of exploitation typically occurs when the victim requests a shared network resource via Server Message Block (SMB), which is non-existent or the IP of which is unknown, and where access authentication is performed using the challenge/response protocol NTLM (NT LAN Manager); although Kerberos authentication has been around for many years and the default protocol in the latest Windows distributions, the use of NTLMv2 is still widely used in corporate enterprise systems today because it must be used for authentication on systems configured as members of a workgroup, for local login authentication on non-domain drivers, or non-Microsoft applications.
In this case, the attacker will have responded to the name resolution query initiated by the victim via LLMNR, naming himself as the recipient, and receiving the victim's credentials: username and password hash. This password hash corresponds to the hash of the credentials in clear using an MD4 hash algorithm without a jump and is therefore considered cryptographically insecure.
Another particular case occurs when a client on the local network enters an unknown URL address in its browser, and the browser is configured with the network option "Automatic configuration detection" (or similar depending on the browser); in this case, the browser will try through LLMNR to find a host called WPAD (Web Proxy Autodiscovery Protocol) from which to request a file named wpad.dat containing the proxy's automatic configuration data. In this case, the requesting client is tricked by the attacker who shows him a false authentication window to obtain the requested file, thus providing his credentials in clear. Likewise, the attacker could impersonate the network proxy and thus have access to the entire data flow of the victim's network traffic.
Thus, as we have seen very briefly in the cases mentioned, from the moment the attacker (the host we have called ATTACKER in the image above) has supplanted the legitimate recipient via LLMNR/NBNS, he will already know the username and at least the hash of the victim's password.
As we have seen, this type of attack requires having previously gained access to the internal network. Once the attacker is on the internal network, he will use and leave acting for hours or even days some tool such as Responder or Inveigh, which will capture all possible network traffic, responding fraudulently to LLMNR/NBNS requests, and simulating services that require credentials, such as SMB, DNS, LDAP, IMAP, FTP, SQL, HTTP, HTTPS, etc., in an attempt to capture that traffic and respond by its known ports.
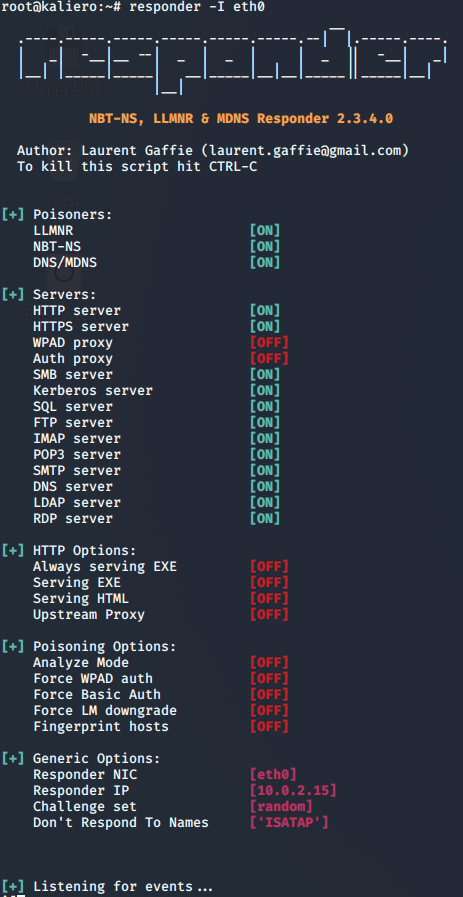 As a result of the execution of these tools, the attacker will obtain the user and usually the password hash. With this, the only thing left to do is to recover the password with a specific tool, usually HashCat.
As a result of the execution of these tools, the attacker will obtain the user and usually the password hash. With this, the only thing left to do is to recover the password with a specific tool, usually HashCat.
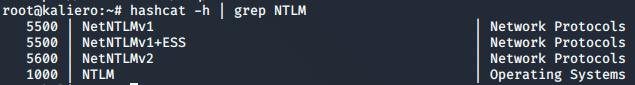
Once a network user's full credentials have been obtained (username + password), a potential attacker will resort to exploiting other types of attacks that require prior authentication, to gain access to the rest of the network's credentials and the resources they protect.
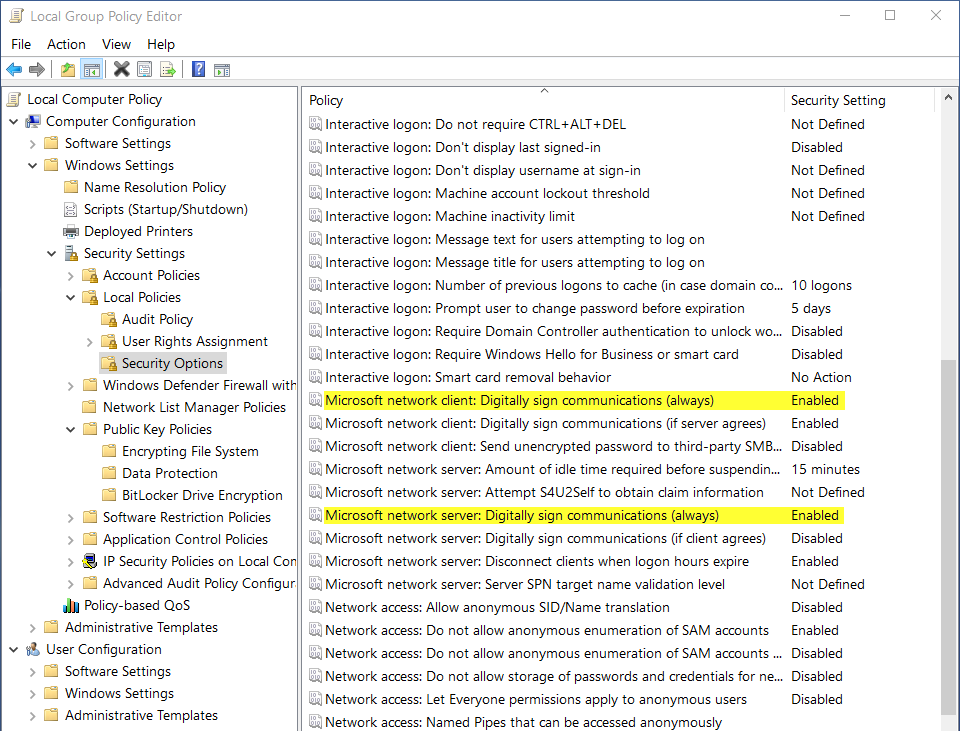
To avoid this series of vulnerabilities due to poor configurations and their consequences, we should establish the following secure configuration whenever possible:
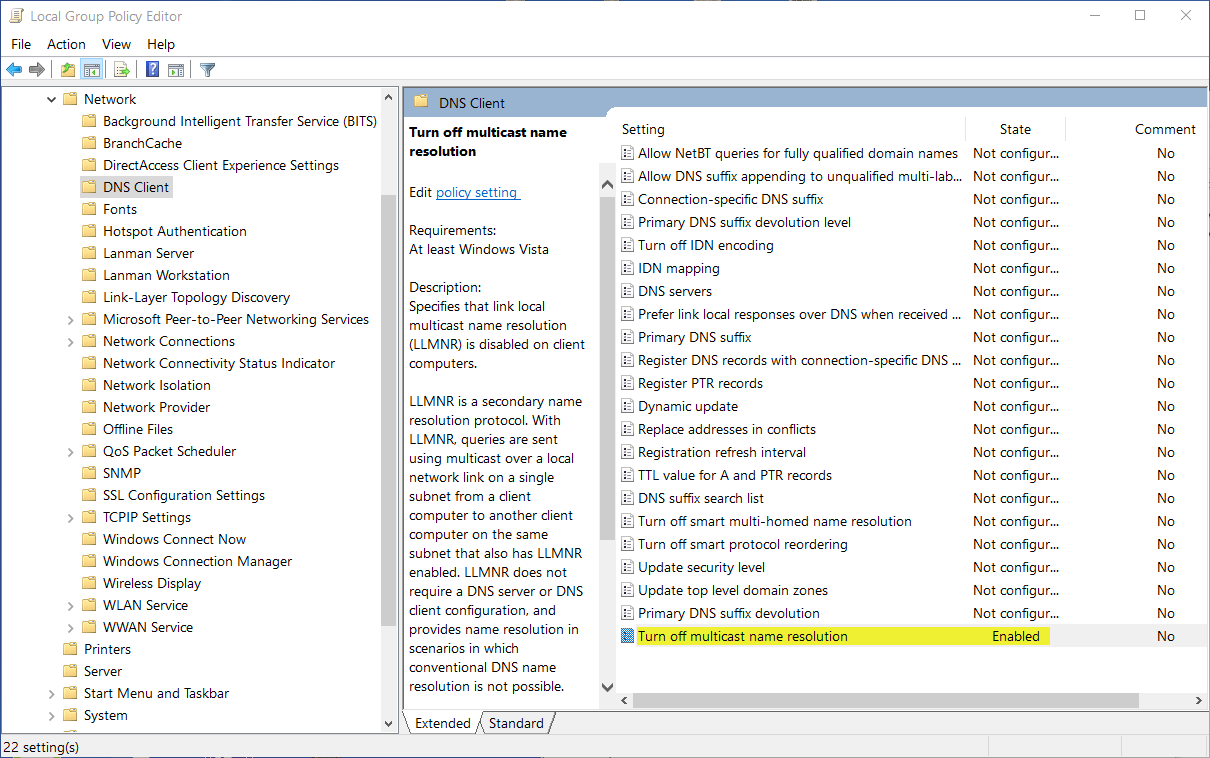
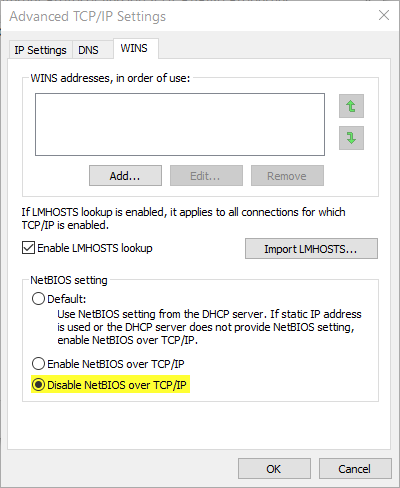 If technical requirements make it essential to keep these two services active (e.g. when we don't have a DNS service deployed), we should at least reduce the impact of this vulnerability by applying controls such as the following:
If technical requirements make it essential to keep these two services active (e.g. when we don't have a DNS service deployed), we should at least reduce the impact of this vulnerability by applying controls such as the following:
 5. Set a static proxy configuration for the browsers used in all clients on the network. In the case of Internet Explorer set the following options:
5. Set a static proxy configuration for the browsers used in all clients on the network. In the case of Internet Explorer set the following options: 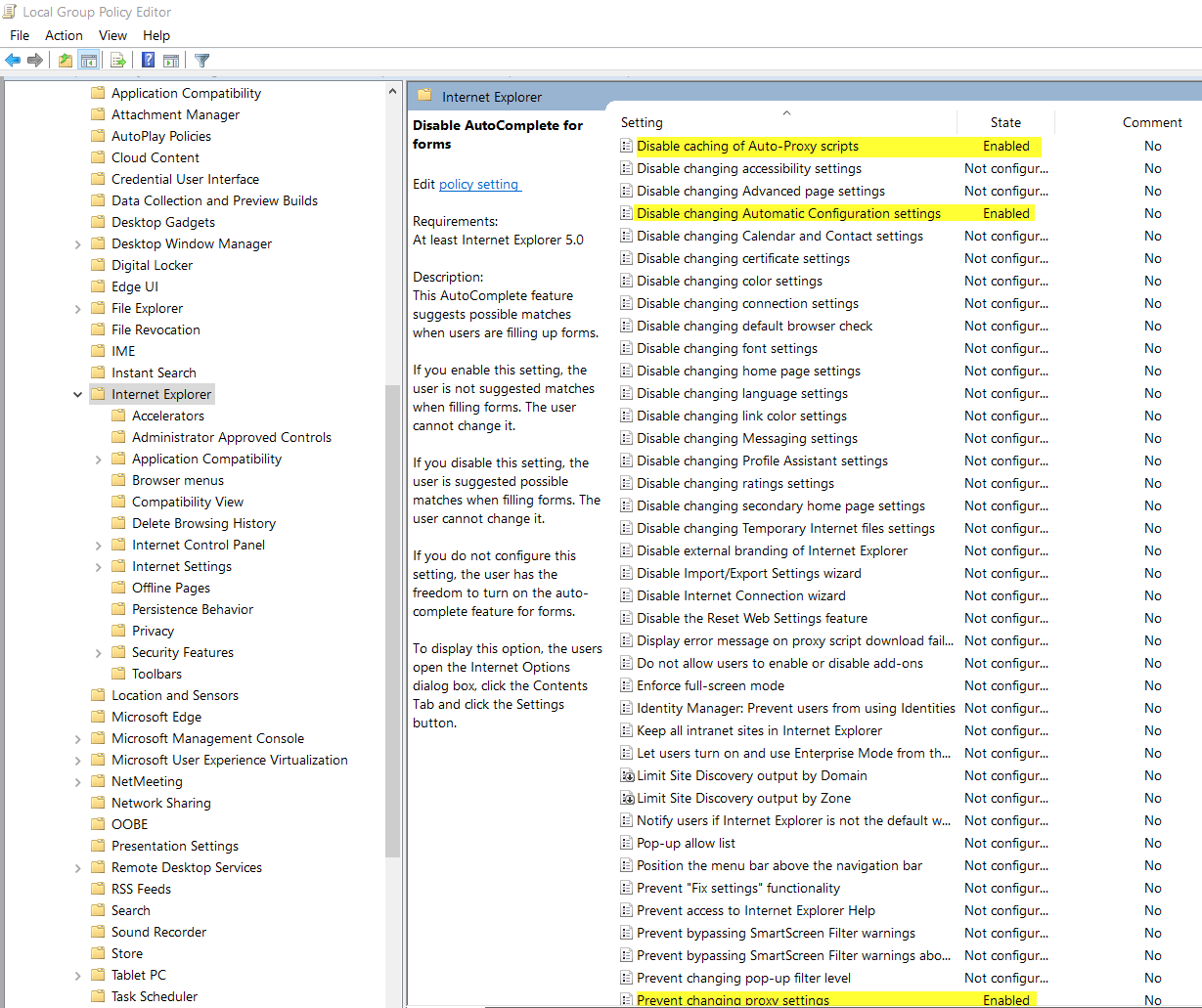
6. Create your own DNS entry for the WPAD host, even if you do not deploy a proxy server in your network.
a. In Domain Controller go to DNS.
b. In the existant domain: add New Zone, Primary Zone:
i. Zone name: wpad.
c. In the new zone, right click it and select New Host:
ii. Name: wpad
iii. IP address: IP of our server hosting the file wpad.dat
Advantio has the necessary expertise to help you with all things security! Focus on your core business, and let us be your security partner.
References:
[1] Dishan Francis (2017). Mastering Active Directory. Packt Publishing Ltd.
[2] https://tools.ietf.org/html/rfc4795 [2] https://docs.microsoft.com/en-us/previous-versions//bb878128(v=technet.10)
[3] https://cccsecuritycenter.org/remediation/llmnr-nbt-ns
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
I am the Senior Security Consultant in Advantio. I have more than 10 years of experience working mainly in the Spanish market. My information security background includes system administration, consultancy, risk advisory services for technology, compliance and legal, design and development of documental frameworks, among others.
CISM, CISA, CRISC, PCI QSA, QSA (P2PE), ISO 22301 LA, ITIL F
Comments