11.2.2 Perform quarterly external vulnerability scans, via an Approved Scanning Vendor (ASV) approved by the Payment Card Industry Security Standards Council (PCI SSC). Perform rescans as needed, until passing scans are achieved.
An Approved Scanning Vendor (ASV) is an entity that can perform ASV scans that will validate adherence to the external scanning requirement as per PCI DSS Requirement 11.2.2. The ASV must be approved by the PCI SSC and will then be added to the list of Approved Scanning Vendors.
Quarterly external vulnerability scanning must be performed by a PCI SSC Approved Scanning Vendor (ASV). This is because external networks, which are part of the PCI DSS scope, are exposed to a greater risk of compromise by malicious users (greater probability of attacks, the greater number of potential attackers, etc.). So, a strong scanning program ensures you can address security vulnerabilities on time.
Obtaining ASV PASS scans every quarter in the right way is one of the most pressing and worrisome obligations that a PCI DSS compliance entity has to accomplish. Several ambiguous points can cause mistakes and confusion. We’ve outlined the two most common ones here.
To Whitelist or not to Whitelist - That is the question
External targets of an entity can be reached from public source IPs. In some cases from any IP, but more often than not only from specific IP addresses. If that’s the case, the ASV scan could result in: FAIL ASV scan (e.g. due to scan interferences), incomplete ASV scan (e.g. due to host(s) detected as not alive), etc.
So, should the scanned entity whitelist ASV scanner IPs?

The response isn’t just a Yes or No
ASV scanners must be allowed to perform scanning without interference from “active protection systems”. “Active” here means security systems that dynamically modify their behavior based on information gathered from non-attack network traffic patterns. These systems include IPS, WAF, QoS, and even Firewalls that block IP addresses upon detection of a port scan (not static rules).
What about Firewalls and their static rule?
In general, static rules on network devices don’t need to be changed to perform an ASV scan in a PCI DSS compliant way.
If ‘host not alive’ or ‘scan interference’ issues persist after whitelisting the ASV scanner IPs on active protection systems, a solution exists.
Then the configuration of the ASV scan and devices can performed in way devices can be performed in a way that the host is found as alive and without any interferences. This usually can be done with scan/device temporary settings, which include:
- Customize TCP discovery
- Customize UDP discovery
- Enable ICMP
- Change firewall closed port behavior from drop to reject
If the above is not possible, there is another way: The ASV customer has to provide the proper evidence to support their assertion that the scan was not actively blocked. And if the ASV agrees that the scan was not actively blocked, it may determine that an additional scan is not necessary. This means involving ASV support (likely each quarter).
Quarterly ASV scans and Remediation scans – When and Why
It’s important to understand what a quarter is. By definition, a quarter refers to the division of a year into four equal parts. So, the following are all valid ASV scan quarters in 12 months:
-
Cycle 1:
- From January to March
- From April to June
- From July to September
- From October to December
-
Cycle 2:
- From February to April
- From May to July
- From August to October
- From November to January (next year)
-
Cycle 3:
- From March to May
- From June to August
- From September to November
- From December to February (next year)
The first quarter is the quarter in which an entity performs the first ASV scan.
A PCI DSS compliant entity has to obtain 4 PASS ASV scans every quarter. This means that if your ASV scan results in a FAIL, you will have to perform the relevant remediation ASV scan in the same quarter of the failed ASV scan until a pass scan is achieved.
Let’s see an example to clarify. Consider we have the following quarters:
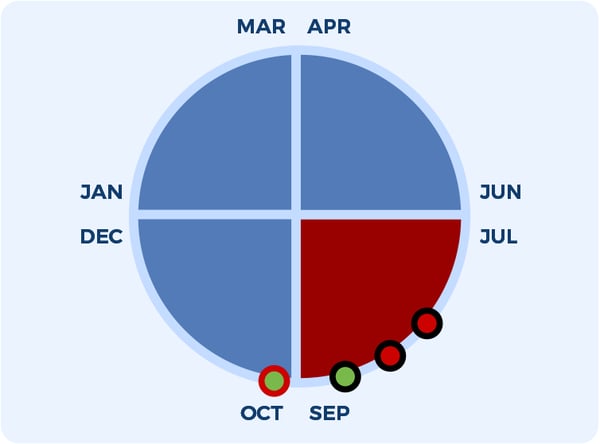
The current ASV scan quarter is in red (Jul-Sep) and:
- We perform the first quarterly scan (first black-red circle) and it results in PCI FAIL.
- Then we perform a remediation scan (second black-red circle) and it again results in a FAIL.
- If we fix the vulnerabilities discovered, the following two cases can be observed:
A. We perform the remediation scan again within September (third black-green circle). This remediation scan is valid for the RED quarter as a PCI PASS ASV scan.
B. We perform the remediation scan again in October (the fourth red-green circle). This remediation scan is NOT valid for the RED quarter thus leaving a quarter without a PASS ASV scan, and the entity could be found not PCI DSS compliant.
Reaching PCI DSS Compliance
For any entity wishing to become or maintain their PCI DSS compliance and certification, they must understand PCI DSS standards, guidelines, and best practices. This is in addition to understanding each related industry standard and its best practice. Yet, this will not be enough. Experience gained from encountering and solving issues is invaluable. It outlines each step an entity has to perform to reach PCI DSS compliance.
Advantio have been recognized as Europe’s second most selected QSA provider among fin-tech service providers. We possess best in class expertise, underpinned by numerous industry certifications and designations, including but not limited to PCI DSS, PA-DSS, PCI PIN, PCI 3DS, P2PE, ASV, GDPR, ISO27001/22301, SOC2, and ACMA (CMMI).
Our subject matter expertise and services focus on cybersecurity, data protection, risk and compliance with a distinct specialization in the ‘Payment Card Industry.’



















Comments