Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

The Payment Card Industry Data Security Standard (PCI DSS) is a continuous process (asses-remediate-report) and a vital part of a company's security dealings. But it's also extremely complex to follow, understand and put in place for many organisations. Furthermore, sometimes it is difficult for PCI DSS specialists to describe the benefits of the PCI Standard in a clear way, when dealing with Clients that do not understand its technical aspects and how to plan each task.
Realising these and other challenges, the PCI Security Standard Council have put together a document called the Prioritized Approach which aims to be a helping hand when it comes to getting organisation up to speed with achieving, monitoring and maintaining their PCI compliance.
In order to protect yourself from card fraud and to keep your money safe, it is vital that you know more about this technology. This article breaks the topic down for you and also teaches you some important methods for preventing card fraud.
The PCI Council kept the Prioritized Approach document up to date each time new requirements of the PCI Standard were released. The latest version of the document is available here.
As stated by the PCI Council themselves, there are some key goals they had in mind when they created this document:
The PCI SSC recognises that those in charge of securing, protecting and keeping cardholder data safe may have no idea where to start and so the PCI DSS Prioritized Approach can:
"help stakeholders understand where they can act to reduce risk earlier in the compliance process"
Additionally, the document is:
"suitable for merchants who undergo an on-site assessment or use SAQ D."
And not only does the document create a better understand of what compliance means and how merchants can achieve it but, as the name suggests, it can also aid them in prioritising certain requirements and it gives them tangible objectives and achievements.
As mentioned, the Prioritized Approach is designed to be a 'helping hand'; like a walking stick to lean on or a friend shouting words of encouragement and advice from the sidelines. But what it is absolutely, under no circumstances meant to do is replace the list of PCI DSS requirements, nor is it designed to replace the entire PCI compliance structure.
Although the document can aid merchants and security teams on the long road to compliance, it's really important to understand that even if you get through one or even five of the document's six milestones (scroll down for a more detailed explanation on that), that doesn't automatically make your company PCI compliant, it just means that you're doing a good job of getting there.
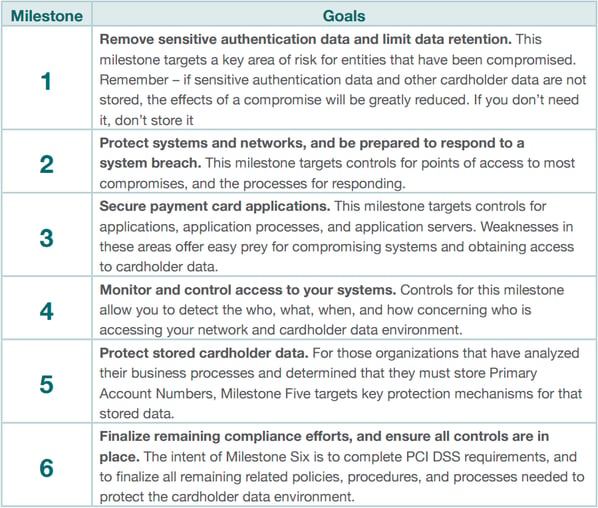
The PCI DSS Prioritized Approach document is structured in an easy-to-digest way. First, it outlines six different milestones:
These milestones have numbered labels too and they have been added to the list of requirements, next to the requirements that pertain to them. For example, when we look at requirement 9.9 - and more in details to its sub-requirements - we notice that they are labelled with a number 2, which reminds us to:
"Protect systems and networks, and be prepared to respond to a system breach. This milestone targets controls for points of access to most compromises, and the processes for responding."
Labels are a short description about what to expect from a particular requirement but, as said already, they do not replace the official instructions of the standard.
The numbered labels are colour-coded which should save you time as you won't have to keep going back to the milestone table that the PCI SSC has laid out for you.
This approach merchants to plan for identified problems better (in terms of manpower and finances). So for example, if you really want to prioritize your response to a system breach then you can put all of your resources into that, following the labelled requirements to tell you exactly what you need to do.
If you're a small to mid-sized business, this is especially handy as you will not spread yourself (or your resources) too thin and it allows you to get things done instead of starting (and not finishing) lots of tasks.
The document helps IT security teams in completing PCI DSS related tasks. And while this was probably the first goal of the PCI SSC when they created and published the document, imagine how it can also support companies in the IT Security industry that offer consultancy or products that help entities in achieving, monitoring and maintaining their PCI compliance.
Take a look at this complementary Excel Tool created by the Council to help IT Security teams to plan tasks.
As a consultant or someone who provides PCI DSS to entities, this document is useful for you too as it allows you to stress the importance of PCI compliance better as merchants will be able to have a much firmer grasp on what the PCI DSS actually is and why they need it. As a result this supports you and your consultancy services and it can even be used as a tool to help you sell your PCI compliance services.
As mentioned, although the document makes life easier, we think that it is merely a step towards PCI compliance. With PCI compliance being mandatory for all business that store, process and transmit cardholder data, the document is a welcome tool from the PCI SSC but there is still lots that must be done once the requirements have been completed.
What is your opinion? Take the survey now.
It is important to remember that, even when you've fulfilled all of the milestones and requirements for compliance, you still need to be assessed by a qualified company (QSA) and compliance is a continuous process too as you need to be reassessed regularly - according to the type of business you run - to ensure that you are still keeping inline with the PCI DSS' requirements.
Advantio is not only a qualified security assessor that can assess whether or not you are PCI compliant, our team of QSAs and Software Development experts is also the creator and unique owner of ZeroRisk Solutions, a line of PCI compliance products that includes:
Those products are able to support entities achieving, monitoring and maintaining compliance in an easy and cost effective way. Take a look at them and talk to us in case you have questions.
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
Marketing Director at Advantio. The articles published in the Advantio Blog have the goal of supporting our mission: making IT Security simple for everyone.
My intention is to discuss IT Security related topics with the eyes of a non technical person, speaking a simple language and trying to show to the readers the benefit of IT Security best practices.
Comments