Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

As with most cyber-attacks, phishing emails are the first point of contact, which can deliver malicious software and compromise both the host and company network regardless of where they land.
Among the most active malware that leverages the naivety of end-users to get delivered, there is Emotet. Emotet is a sophisticated and destructive malware that is primarily spread through phishing emails. Once installed on a victim's computer, Emotet can steal sensitive information, such as usernames and passwords, and can also download and install additional malicious software. Emotet is particularly dangerous because it can propagate itself through a victim's network, allowing it to infect multiple computers and cause widespread damage. In addition, Emotet is known for its ability to evade detection by traditional antivirus software, making it a formidable threat to organizations and individuals alike.
The Advantio SOC team recently discovered an Emotet downloader attached to a suspicious e-mail with an archive (ZIP) attachment.
In this article, we summarize the steps taken by our experts to analyze the artifacts and the steps that every company should take to mitigate these types of attacks.
Emotet is known to deliver itself through an e-mail that often contains a password-protected ZIP file as an attachment, a simple phrase such as “please see attached file” in the body, and the required password to open the ZIP archive.
In this case, the Advantio team couldn’t immediately recognize the e-mail as being part of the widely known Emotet campaign because the modus operandi was slightly different: the e-mail analyzed did, indeed, contain:
1. a zipped file
2. a suspicious subject: a “Tr:” with no further info after the colon
3. a very basic “Yes, thank you” in the body.
The attachment, though, was not password-protected and, thus, there was no suspicious clear-text password in the body of the e-mail.
Nonetheless, it did look suspicious: the recipient wasn’t expecting anything of the sort.
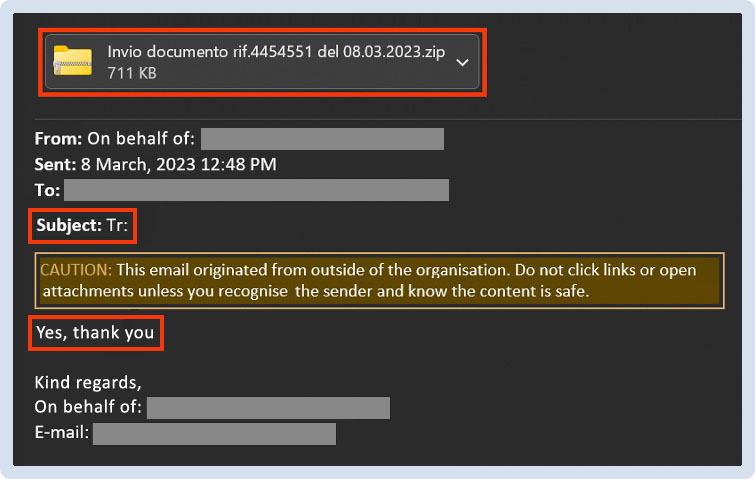
Figure 1 - E-mail
Once the Advantio SOC team confirmed that the e-mail was not expected and, thus, had to be deemed malicious, the Advantio Malware Analysis Team was engaged to safely analyze the attachment.
The archive was unzipped in a protected malware analysis environment and the team was immediately warned by the huge size (more than 530 MB) of the .doc file it contained. A binary check of the file disclosed a fatty “NULL”-section at the end of the file.
This is a tactic many attackers use to avoid the sandbox analysis that most EDRs include in their protection plan: most sandboxes can’t analyze files that are bigger than 500 MB.
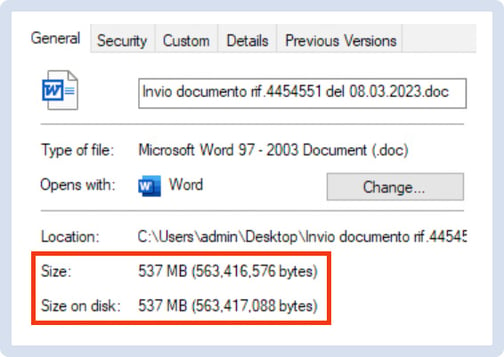
Figure 2 - Word Document Style
The big size of a Microsoft Office file can also be an indicator of the presence of - potentially malicious – “macros”. Macros are code-based automation tools that can be included in any Microsoft Office file. Many attackers can use macros to deliver their malicious code to the machine of the unfortunate victim.
Through a quick static analysis, the team was able to confirm their hypothesis: the .doc included an embedded code (OLE2) component and a call to Visual Studio DLLs.
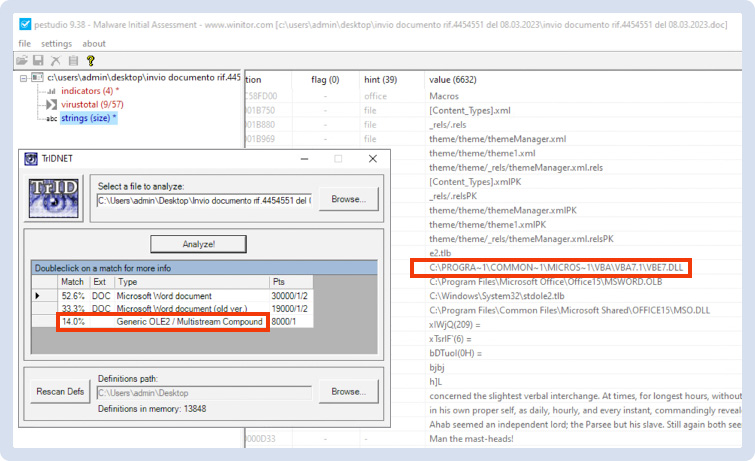
Figure 3 - OLE2 Evidence
Moreover, the document included more than 10 potentially malicious macros.
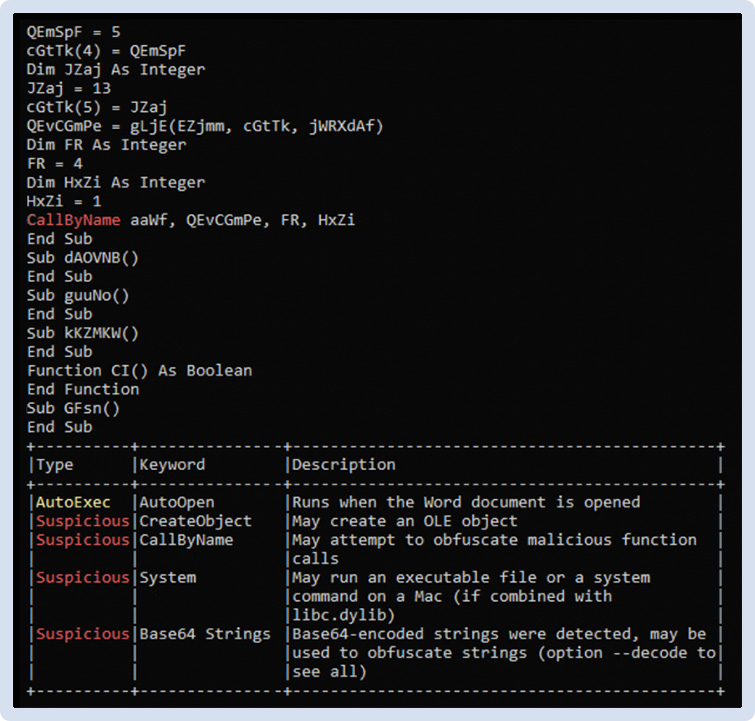
Figure 4 - OleTool Results
When opening the document with Microsoft Word, the user gets prompted to “Enable Content”.
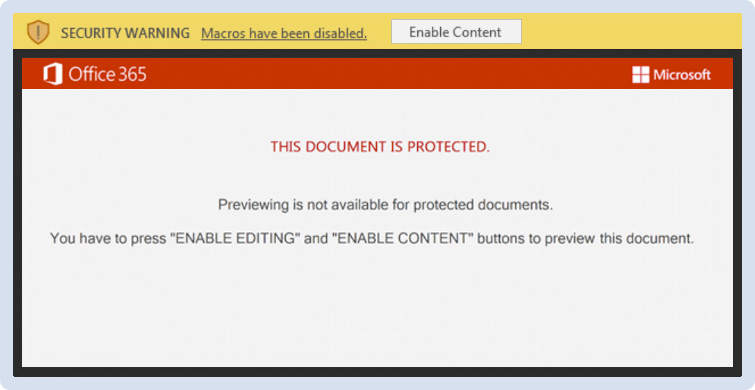
Figure 5 - Word Document Opening
To perform a deeper, dynamic analysis of the file, the Advantio team enabled code execution. They immediately noticed a new explorer window being opened, indicating that the system was downloading a DLL file.
At this point in the analysis, the team could be sure: the attachment was, indeed, a malware downloader.
The Advantio Malware Analysis Team carried through with the analysis of malware behavior and collected numerous IOCs (listed at the end of the article).
With no need for any further action from the user, the downloader wrote a DLL on the system and assured its persistence on the victim’s host by modifying the “Autostart” MS Office registry key.

Figure 6 - Autostart RegKey
The malicious DLL was downloaded from the following URL:
http://ly[.]bi3x[.]org/magazini/pWKy5V5/?224421&c=1
In this stage, though, the downloader tried to contact several different domains until the malicious DLL has been downloaded.
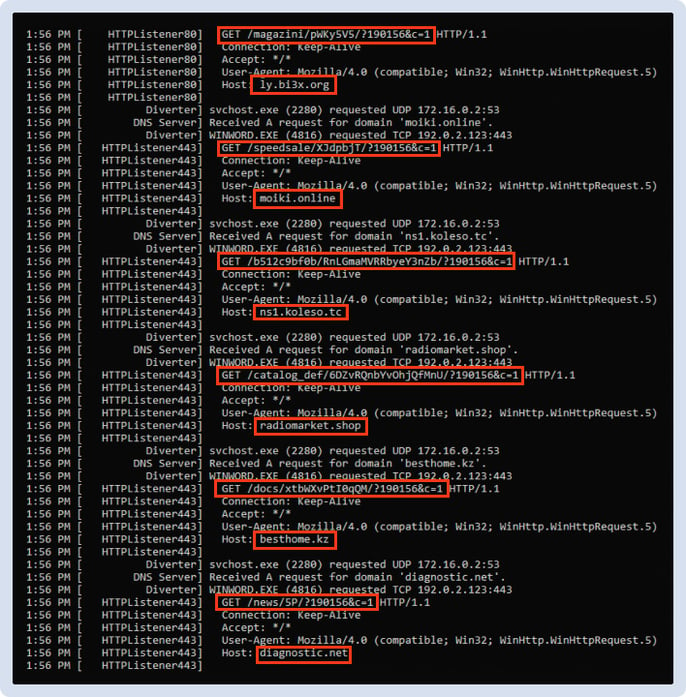
Figure 7 - Domains sweeping
Right after this phase, the second stage of the malware runs a “regsvr32” instance, which begins contacting a Command-and-Control server (91.121.146.47).
The C2 instructs the malware on board of the machine to collect system and network information and send them to the C2 server. The malware has been observed writing all the useful info in two temporary files.
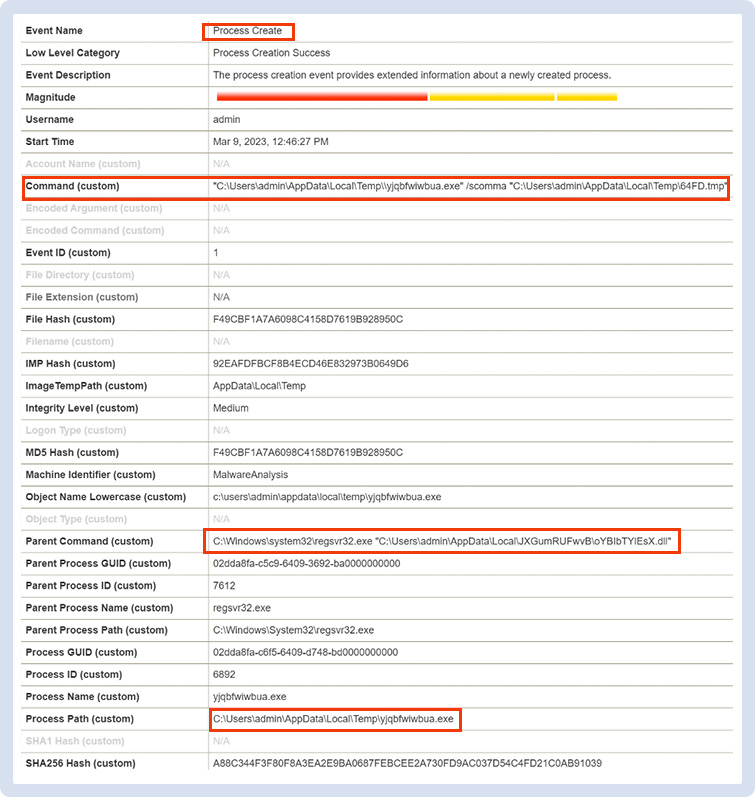
Figure 8 - Tmp File Created
In a short period of time, our now infected system has been observed contacting 5 different C2 servers, presumably sharing the same system and network information that it collected before. Even after killing the process, the system continued establishing the connections to these servers.
It then started connecting with more than 30 different IP addresses on 7080 and 8080 TCP ports. Click here to download a detailed screenshot.
All 5 C2 servers are known in the cybersecurity community to be associated with an Emotet variant. This is when Advantio Malware Analysis Team could associate the malware just analyzed with the well-known Emotet malware family.
The most effective response to this kind of attack is not to open the attachment: as this analysis has made evident, the sole action the malware requested from the user to be (un)safely delivered was to open the file and enable the embedded code execution. After the user enabled its execution, the malware operated entirely in the background, undetected by the user.
For complete protection of your company's endpoints, it’s recommended to deploy an EDR (Endpoint Detection and Response) solution on each device.
Advantio SOC Team tested one EDR Solution (Bitdefender) on this malware, and it successfully detected and blocked the threat. As shown in the image below, the EDR disinfected the Word document as soon as the user tried to access it, blocking the malware before the initial download.
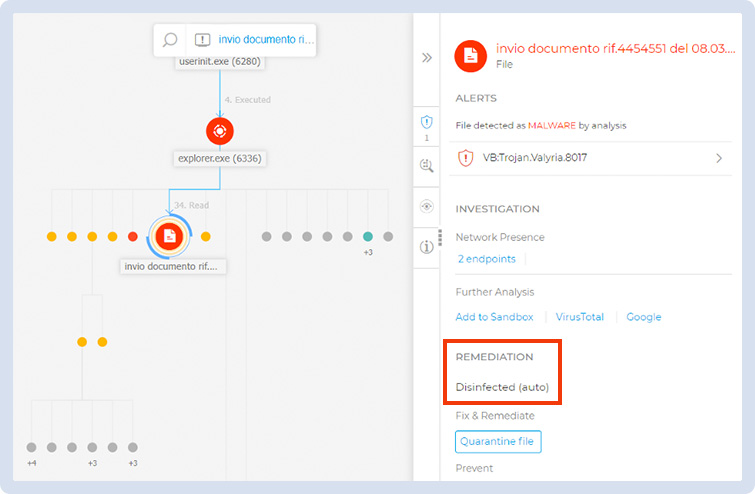
Figure 9 - Bitdefender graph
This is a perfect example of why it's crucial for individuals and organizations to prioritize security awareness. By investing in security awareness training, you can learn how to identify and respond to potential security threats. This will enable you to protect your personal and sensitive information and contribute to a safer and more secure digital environment. Whether you're an individual looking to safeguard your personal data or an organization looking to protect your assets and reputation, security awareness is a critical component of your overall security strategy.
Take control of your security posture today by prioritizing security awareness.
I would like to mention and thank Silvia Guma (SOC Analyst L2 at Advantio) for her contribution to this analysis as this would not have been possible without her.
MITRE ATT&CK
|
Account Discovery |
T1087 |
|
Archive Collected Data |
T1560.002 Archive via Library |
|
Boot or Logon Autostart Execution |
T1547.001 Registry Run Keys / Startup Folder |
|
Command and Scripting Interpreter |
T1059.003 Windows Command Shell |
|
Credentials from Password Stores |
T1555 |
|
File and Directory Discovery |
T1083 |
|
Input Capture |
T1056.001 Keylogging |
|
Native API |
T1106 |
|
Network Share Discovery |
T1135 |
|
OS Credential Dumping |
T1003 |
|
Process Discovery |
T1057 |
|
Remote System Discovery |
T1018 |
|
Subvert Trust Controls |
T1553.002 Code Signing |
|
System Information Discovery |
T1082 |
|
System Network Configuration Discovery |
T1016 |
|
System Owner/User Discovery |
T1033 |
|
User Execution |
T1204.002 Malicious File |
|
Windows Management Instrumentation |
T1047 |
IOCs
All collected IOCs are listed below:
|
IP ADDRESSES |
1.234.2.232 101.50.0.91 103.132.242.26 104.168.155.143 107.170.39.149 110.232.117.186 115.68.227.76 119.59.103.152 147.139.166.154 149.56.131.28 153.126.146.25 153.92.5.27 159.65.88.10 160.16.142.56 163.44.196.120 164.68.99.3 167.172.199.165 167.172.253.162 169.57.156.166 172.105.226.75 173.212.193.249 183.111.227.137 185.4.135.165 197.242.150.244 202.129.205.3 206.189.28.199 45.235.8.30 66.228.32.31 72.15.201.15 79.137.35.198 82.223.21.224 91.121.146.47 91.207.28.33 95.217.221.146 |
|
DOMAINS |
Ly[.]bi3x[.]org moiki[.]online ns1[.]koleso[.]tc radiomarket[.]shop besthome[.]kz diagnostic[.]net |
|
TCP PORTS |
8080 7080 |
|
HASHES |
65D2FEA34B5EAD55F85670E48C686DE4421954C4FD235F5247D60F43D205114E |
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
My experience in information technology spans over 20 years. For the past six years, I have worked as a Security Analyst, Malware Analyst, and Digital Forensics Analyst. In addition to my background in IT systems administration, I am also a network engineer. I love Cyber Security because it reminds me that I never know enough.
Comments