Allowing people to pay for goods without inserting their card into a card reader, contactless payments help to make transactions faster and make customers’ life easier. But as millions of people use these cards, there are also many malicious individuals in the world looking to take advantage.
In order to protect yourself from card fraud and to keep your money safe, it is vital that you know more about this technology. This article breaks the topic down for you and also teaches you some important methods for preventing card fraud.
Each transaction can be completed in seconds.
In short, contactless payment works by simply holding or placing the card (also known as smart payment card) next to a point of sale (PoS) device enabled for this type for transaction. After a few seconds, the machine will automatically allow the transaction to go through and the purchase will be completed.
From a technological point of view, each smart card is fitted with a minuscule computer chip along with an - also incredibly small - antenna. These will generally use either radio-frequency identification (known as RFID) or near-field communication (NFC) to transmit data to the point of sale device and make the secure transaction happen.
Make sure you know what your card can do.
Contactless cards like these are usually adorned with the four-lined signal indicator, as explained here.
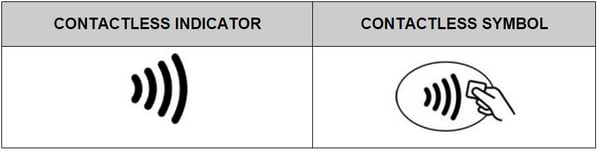
Additionally, you may notice a sticker attached to the front of your card which will tell you that you have such a card in your hands. If your card makes no mention of this and if it does not have the four-lined signal indicator on it, then you may contact your bank and find out more.
As for figuring out whether a retail establishment accepts smart payment cards, many stores put up symbols or notices informing you whether or not they are equipped for such transactions or their point of sale devices will have a notice on its screen (see imagery above). If the store does not currently accept those payments, it is highly likely that they will do so in the future. Looking at the industry, experts highlight a fast rise of NFC payment tech with smartphones (e.g. with Apple Pay and Android Pay) and so it is probable that more retailers and establishments will support the technology soon.
Is it really convenient to use these cards?
The main and perhaps the most obvious advantage to smart payment is that it can save you and the cashiers a huge amounts of time. Putting your card into a card reader, entering your PIN and waiting for your transaction to be processed can take a few minutes. While saving 90 seconds or so thanks to your smart card may not sound huge on paper but when you're buying your coffee in a rush because you're late to the morning meeting, you will really appreciate it.
Another benefit is the fact that you don't have to enter your PIN and therefore you won't need to worry about being under the watchful eyes of potential fraudsters around you while typing it into the keypad. You will definitely still need your PIN for banking operations and for transactions that involve a large amount of money because, as explained in the next paragraph, not everything can be bought with contactless payment cards.
Your PIN Code won't be needed at all in case you use a Chip-and-Signature type of payement, which is different from the Chip-and-PIN described in the previous paragraph. Most of the EMV cards used in US are currently based on the Chip-and-Signature method.
A great technology with some risks involved.
Anyone who has one of these cards in their hands can purchase products or services. This is why banks have set transaction thresholds designed to stop fraudsters from taking someone's card and running up a high bill (in the UK the limit is £30, while in the United States it is $25 USD), though some outlets such as pharmacies allow higher payments, authorised with a signature. This is an important measure to reduce the losses for negligent cardholders.
Furthermore, this technology has led to sensitive information being hacked from cards, with malicious people going into public spaces and using wireless devices that are designed to get the card number, info about recent card transactions, and the expiry date from cards, which they are able to do just by standing on close proximity to the card. An example comes from Trendmicro’s Blog, explaining how hacking RFID Cards was possible with Android app. Another example was brought to the audience during the Hack In The Box Security Conference that took place on May 2015 in Amsterdam. during this event “Ricardo J. Rodriguez and Jose Vila presented a demo of a real world attack, to which all NFC capable Android phones are vulnerable”.
And while the CVV security code isn't accessible hacking cards in this way, and that's what's generally needed in order to make online purchases, an experiment from consumer group Which? showed that they were able to use stolen card details, along with a fake name and address, to buy a £3,000 television from one site which didn't require a CVV code. This experiment shows us that there is still a huge gap of knowledge between what the information security industry says and what merchants actually do to protect their customers.
Best practices for smart card owners.
While the benefits may greatly outweigh the risks, it is still important that you are proactive about protecting your payment card and you get to know everything about it. One of the most common ways in which you can do this is simply to wrap your contactless payment card in aluminium foil or buy a specially made protective wallet.
As for the phone-hack method of card fraud, it is advised that if you aren't using the NFC capabilities on your phone if not needed. You should turn them off when you are around; this will also help your phone conserve battery and it is a win-win. Also, it is advised that you do not download apps that haven't been listed on either Google Play or on the Apple App Store, as these may contain malicious software.
Additionally, keep in mind that you are able to report any fraudulent transactions to your bank so, if your card goes missing or you see odd transactions on your statement, you should give your bank a call and express your concerns.
And finally, make sure your favourite stores are protecting their card-reading devices by following the rules set by the industry’s authorities. Remind them that a faulty or manipulated card-reading device can cause losses of data, personal information and, consequently, money.
















Comments