📣 Big announcement: we have now been listed on the SWIFT Customer Security Programme (CSP) Assessment Providers directory.
Contact us now to validate your compliance posture with SWIFT CSP requirements:
The exchange of goods has always been present in the history of mankind and is a fundamental part of the economy. With the arrival of banks and savings banks as custodians of assets, the need to guarantee the safe movement of money between accounts arose. Initially, these financial movements were recorded manually, resulting in delays, transcription errors, and fraud.
With the advent of telegraph-based telecommunications, the time associated with the processing of this type of transaction (called "Telegraphic Transfers" or TT), typically took between two and three business days to be processed, especially in asset transfers between financial institutions located in different parts of the world (international transfers), was optimized. These times in interbank operations were minimized with the evolution of telecommunications networks, without the need to physically exchange money and using only electronic records, a process called "electronic funds transfer" or EFT.
Initially, interbank transfers were managed directly between the two entities involved in the transaction (sender and receiver). However, given the number of banking entities in the world, the management of one-to-one transactions became a titanic task, whose only solution was the use of an intermediary entity acting as a concentrator or "hub" for the routing of transfers.
In response to this need, the Society for Worldwide Interbank Financial Telecommunication (SWIFT) was founded in 1973 in Belgium, a cooperative entity composed at that time of 240 banks in 15 different countries, whose objective was to serve as an intermediary for the execution of financial transfers between banking entities. SWIFT offers not only services related to financial transfers, but also a communications and software infrastructure that facilitates the routing of transactions (or "messages") and the identification of the different entities involved in the transaction, where an alphanumeric system is used to identify each member organization, indistinctly referred to as "bank identifier code" (BIC), SWIFT code, SWIFT ID, or ISO 9362 code.
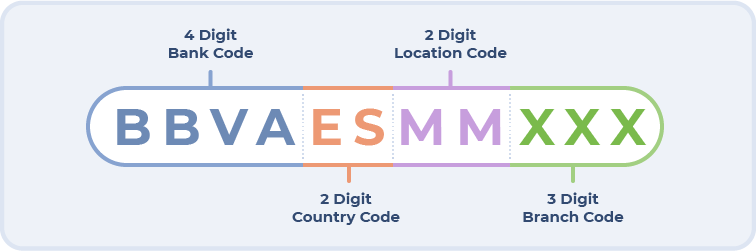
Figure 1. Example of a BIC/SWIFT code
As with any service of this type, not only interoperability and response, times are important, but also security. The SWIFT messaging system requires high levels of protection against unauthorized modification, availability, confidentiality, and the ability to track activities (traceability), since the trust of customers is built on these features. As a result, the SWIFT system was attacked in 2015 (TPBank in Vietnam and Banco del Austro in Ecuador) and 2016 (Akbank in Turkey and Central Bank of Bangladesh), causing millions of dollars in losses and forcing SWIFT to take detective and corrective measures to minimize the impact of future attacks.
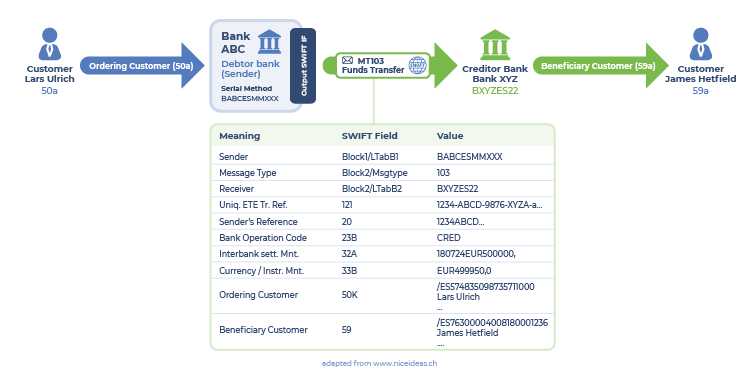
Figure 2. Example of a basic SWIFT transaction
SWIFT Customer Security Controls Framework (CSCF) and Customer Security Programme (CSP)
Due to the attacks on SWIFT's infrastructure, the SWIFT Customer Security Controls Framework (CSCF) was published in 2017, which outlines a series of measures designed to protect the SWIFT network infrastructure. These controls are updated annually to align protection levels with the evolution of both attack techniques and underlying technology:
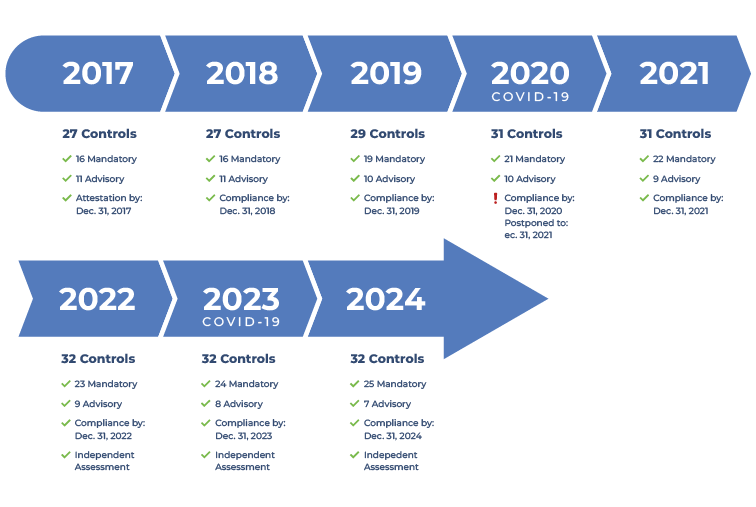
Figure 3. Timeline of SWIFT CSP
These controls are divided into two categories:
- Mandatory controls must be implemented as a priority by each network member in its SWIFT infrastructure at the local level, and
- Advisory controls are a set of best practices that can be implemented on a discretionary basis by the organization but may become mandatory controls in the future depending on the evolution of attacks
The relevant SWIFT CSCF 2024 controls are organized into three main objectives, supported by seven principles and 32 controls, 25 of which are mandatory and 7 of which are recommended:
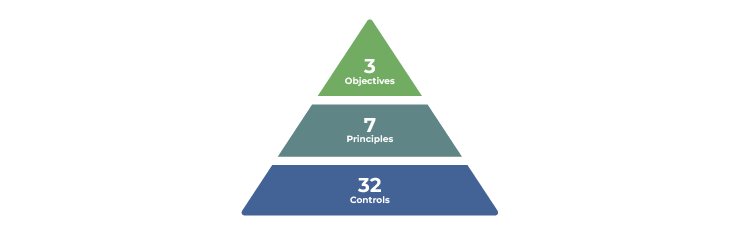
Figure 4. SWIFT CSCF organization
1. Secure your environment:
- Restrict Internet Access and Protect Critical Systems from General IT Environment
- Reduce Attack Surface and Vulnerabilities
- Physically Secure the Environment
2. Know and limit Access:
- Prevent Compromise of Credentials
- Manage Identities and Segregate Privileges
3. Detect and respond:
- Detect Anomalous Activity to Systems or Transactions Records
- Plan for Incident Response and Information Sharing
As a complement to the security controls themselves, SWIFT CSCP also includes a descriptive guide for the identification of services and components within the scope of compliance (including production processing, backup, and disaster recovery locations), different types of component deployment architecture to validate the applicability of controls and assets, a list of risks and their corresponding mapping with their countermeasure, an inventory of example threat scenarios, a table identifying the relationship of SWIFT's control objectives with the requirements of the NIST Cybersecurity Framework, ISO/IEC 27002 and PCI DSS, and a table of shared responsibilities when using services from external providers (including cloud service providers - CSPs).
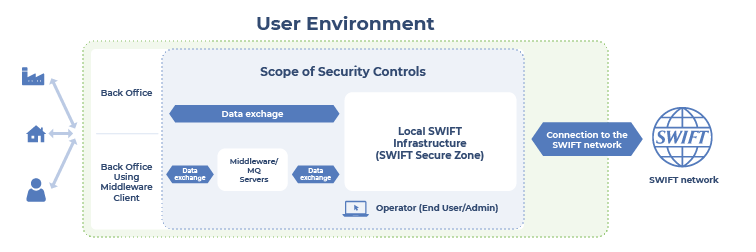
Figure 5. Example of SWIFT CSCF scope of compliance
SWIFT CSCF controls, in conjunction with other documents such as SWIFT Customer Security Controls Policy (CSCP) and SWIFT Information Sharing and Analysis Centre (ISAC), are managed through the SWIFT Customer Security Programme (CSP), which describes the processes for compliance reporting, third party security status verification and follow-up remediation actions for non-compliance.
Implementation and compliance plan
For entities facing the SWIFT CSCF controls deployment process for the first time or organizations that already have some level of cybersecurity maturity, defining an interactive methodology that facilitates the security controls lifecycle will optimize the time and effort in securing the local SWIFT services infrastructure.
In this sense, the recommendation is to proceed in a similar way to that followed in the implementation of other standards: by using the Deming cycle or Plan-Do-Check-Act (PDCA):
- PLAN (P): This phase defines the strategic, operational, and tactical objectives of the process, the administrative and operational tasks required to achieve these objectives, and the identification, sizing, and preparation of all related logistical elements, including:
o Gain senior sponsorship and engage all relevant stakeholders
o Identify both internal and external resources to be involved in the project
o Identify the scope of SWIFT compliance (services and components) and the architecture model that best matches that of the organization
o Identify SWIFT CSCF controls applicable to the environment
o Prioritization of mandatory SWIFT CSCF controls and feasibility analysis of recommended controls
o Identify existing security controls in the environment
o Integration of SWIFT CSCF controls with other regulatory frameworks or security standards applicable to the organization (ISO/IEC 27002, PCI DSS, NIST CSF)
- DO (D): In this second phase, all the tasks established in the PLAN (P) phase are implemented. It is usually the longest phase in terms of time and complexity:
o Implementation of compliance scope minimization activities
o Deployment of SWIFT CSCF Security Controls
- CHECK (C): This third phase verifies that all the tasks performed in the Do phase (H) have been carried out correctly following the defined planning and objectives and identifying any deviations:o Performing internal differential compliance analysis for early detection of non-compliance.
o Performing the independent compliance assessments required by SWIFT CSP
o Compliance report
- ACT (A): in this phase, you should proceed with the correction of any problems encountered and any improvement actions with a view to optimizing the system:
o Correction of non-compliance
o Analysis of the next release of SWIFT CSCF
The monitoring and support of a specialized entity in each of these phases is advisable, as it will ensure that the strategic objectives defined and the associated tactical actions are aligned with the criteria defined by SWIFT CSP, which will minimize the occurrence of unforeseen tasks during the course of the cycle over time, thus defocusing the previously defined efforts.
Compliance evaluation and reporting process
In order to validate that an organization connected to the SWIFT infrastructure complies with the security controls described in SWIFT CSCP, the compliance status of these controls must be reported based on the SWIFT CSP guidelines, which specify that all customers must report their compliance posture using the Know Your Customer (KYC) tool on an annual basis or when there is a change in scope. As of July 2021, this compliance assessment is required to be performed independently without interference from the business units. For this, there are two alternatives:
- Internal assessment: In organizations that implement the three lines of defense model for organizational risk management (operational management, risk and compliance management, and internal audit) and whose level of maturity in terms of cybersecurity is high, the second or third line is allowed to assess the first line of defense, in order to obtain an independent result
- External assessment: In this case, the compliance assessment is performed by an external organization with demonstrable experience in cybersecurity
The compliance report should indicate whether the entity is compliant with the SWIFT CSCF control objectives, will be compliant in the future (which implies an action plan), is not compliant or the control is not applicable. This report will be visible to both SWIFT and the counterparties (financial institutions).
As a result of the SWIFT CSP transparency criteria, if an organization fails to adhere to the SWIFT CSCF controls, other members of the SWIFT community may have access to this information (which will affect relationships with third parties) or the affected entity may be disconnected from the SWIFT network.
How can Advantio help in this process?
Based on Advantio's expertise in payments and cyber security, we offer the following services for implementation and independent assessment of compliance with SWIFT CSCF controls in accordance with SWIFT CSP:
- SWIFT CSP Readiness, where the architectural type and the applicability of each control type to your operating environment are identified (the total number of controls is determined by the "SWIFT architecture type", defined by how SWIFT members connect to the SWIFT network), performing a preliminary review of your current cybersecurity posture to the CSCF requirements, and detecting any gaps within these controls that need improvement, proposing potential remediation steps
- SWIFT CSP Independent Assessment, where our professionals conduct an independent assessment to verify the implementation of the mandatory controls ("satisfied", "partially satisfied", and "not satisfied"), including validation of policies, processes, and business practices according to CSCF requirements and providing the required documentation to show compliance through stakeholders' meetings, documentation review, site visits, and operational review
- Remediation Plan: If compliance gaps are detected, Advantio will assist your team in remediating any issue and maintaining the cybersecurity level in your environment
- Ongoing Support: Advantio offers your company our expertise along the journey to support the disposition of the design, implementation, and effectiveness of the CSCF controls.
For more information, please contact one of our representatives

.png)












Comments