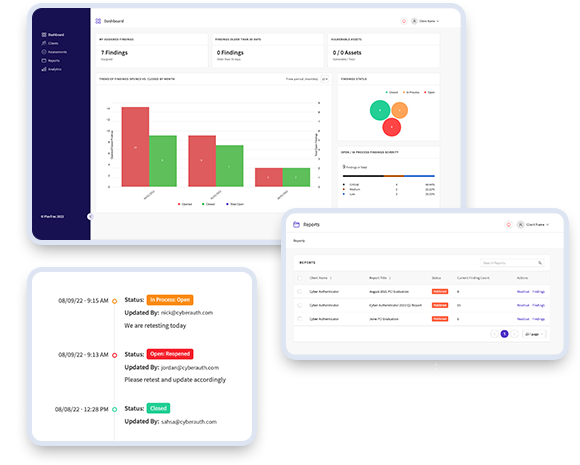
Reporting Dashboard
We also deliver an exclusive premium threat report, accessible solely through the Advantio Vulnerability Portal, offering these exceptional benefits:
- Ability to create custom reporting
- In-app remediation collaboration
- In-app or email notifications when finding statuses change
- Readily review updates in real time
- Role-based access controls
- Analytics that provide a view of all findings and SLAs
- Track remediation status of vulnerabilities
- Supports CSV and PDF export