Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

After more than a year since ISO/IEC 27002:2022 (February 15, 2022) was published, and almost six months since ISO/IEC 27001:2022 was updated (October 25, 2022), there are still some doubts about what these new versions imply.
The purpose of this update has been to reflect advances in technology and industry practices that are constantly evolving. Furthermore, the updated structure is an imperative step toward its simplification and ease of use
In this new version of the standard, we can see that the requirements of ISO/IEDC 27002:2013 are still valid in this new version, and what has been improved is its focus, since it now meets the strategic needs that organizations currently have with the interaction between cybersecurity, information security, and data protection.
We can notice this from the new name of the standard, which inherits the name of the specific committee that developed it: the ISO/IEC Committee JTC 1/SC 27 called "Information Security, Cybersecurity and Privacy Protection":
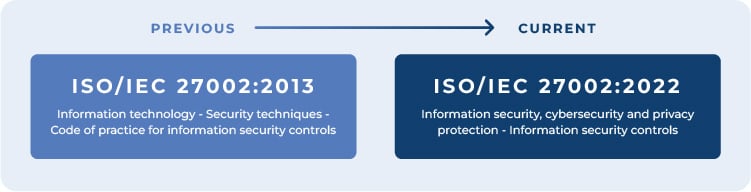
This updated version no longer consists of a code of practice but is instead a reference document that defines a generic set of information security controls that organizations can use within an ISMS based on ISO 27001 or in whatever framework they chose.
What are the main changes?
We can highlight the following changes in this version:
1. New Control Layout
ISO defines ‘control’ as a measure that modifies or maintains risk. Each control in this updated version of ISO/IEC 27002 includes two new elements for better understanding, classification, and implementation. The first is the attribute table (we'll discuss this in more detail ahead) and the second is the purpose of the control. Below is the layout of each control:
|
Controls Structure
|
|
| Control title |
Short name of the control.
|
| Attribute table (New in 2022 version) |
Table that indicates the values of each attribute for the given control.
|
| Control |
Description of the control indicating the requirements for compliance.
|
| Purpose (New in 2022 version) |
Explanation of the need to implement the control.
|
| Guidance |
How the control should be implemented.
|
| Other information |
Additional explanation or reference to other documents in relation to the control.
|
2. Attribute Table of the Controls
An important addition to this updated version is the addition of attributes, which introduce standardized criteria for grouping and filtering controls. The attributes will help to better understand the controls as it adds relevant criteria in the organizational aspect (not only with information security) and integrates known and similar definitions of other recognized frameworks such as NIST CSF.
Each control now has the following attributes:
| Attribute | Explanation | Values |
|
Control type
|
When and How the given control modifies the risk with respect to the occurrence of an information security incident.
|
#Preventive
#Detective #Corrective |
|
Information Security properties
|
Characteristic of the information that will be preserved
|
#Confidentiality
#Integrity #Availability |
|
Cybersecurity concepts
|
Cybersecurity concepts defined in the cybersecurity framework described in ISO/IEC TS 27110
|
#Identify
#Protect #Detect #Respond #Recover |
|
Operational capabilities
|
Practitioner’s perspective of information security capabilities
|
#Governance
#Asset management #Information protection #Human resource security #Physical security #System and network security #Application security #Secure configuration #Identity and access management #Threat and vulnerability management #Continuity #Supplier relationships security #Legal and compliance #Information security event management and #Information security assurance |
|
Security domains
|
Controls from the practitioner’s perspective of information security capabilities
|
#Governance and Ecosystem
#Protection #Defense #Resilience |
As an example of a control structure in ISO/IEC 27002:2022, you can see its attribute table:
| Control type | Information security properties | Cybersecurity concepts | Operational capabilities | Security domains |
| #Preventine #Corrective |
#Confidentiality #Integrity #Availability |
#Protect #Respond #Recover |
#Governance | #Defence |
Control
:
The organization should establish and maintain contact with special interest groups or other specialist security forums and professional associations
Purpose:
To ensure appropriate flow of information takes place with respect to information security.
The updated version of ISO/IEC 27002 has a different structure compared to the 2013 version. As opposed to the 14 domains of the previous version, there are now just 4 categories. The categorization of controls given in Clauses 5 to 8 is referred to as a theme.
Furthermore, the number of controls has been reduced from 114 to 93, divided into the following four categories:
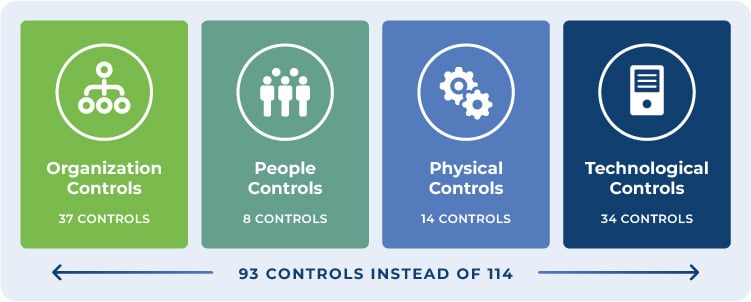
To consolidate the increased number of controls in this version, 11 new controls have been added. Only 1 control from the previous version has been removed, and 57 controls that had similar objectives have been merged into 24 new controls.
The details of the changes are as follows:
New controls:
| Control | Type of control |
|
5.7 Threat intelligence
|
Organizational
|
|
5.23 Information security for use of cloud services
|
Organizational
|
|
5.30 ICT readiness for business continuity
|
Organizational
|
|
7.4 Physical security monitoring
|
Physical
|
|
8.9 Configuration management
|
Technological
|
|
8.10 Information deletion
|
Technological
|
|
8.11 Data masking
|
Technological
|
|
8.12 Data leakage prevention
|
Technological
|
|
8.16 Monitoring activities
|
Technological
|
|
8.23 Web filtering
|
Technological
|
|
8.28 Secure coding
|
Technological
|
Renamed controls:
| ISO/IEC 27002:2013 | ISO/IEC 27002:2022 |
|
6.2.2 Teleworking
|
6.7 Remote working
|
|
9.2.1 User registration and de-registration
|
5.16 Identity management
|
|
9.2.3 Management of privileged access rights
|
8.2 Privileged access rights
|
|
9.4.2 Secure log-on procedures
|
8.5 Secure authentication
|
|
9.4.5 Access control to program source code
|
8.4 Access to source code
|
|
7.3.1 Termination or change of employment responsibilities
|
6.5 Responsibilities after termination or change of employment
|
|
11.1.1 Physical security perimeter
|
7.1 Physical security perimeters
|
|
11.2.6 Security of equipment and assets off-premises
|
7.9 Security of assets off-premises
|
|
11.2.9 Clear desk and clear screen policy
|
7.7 Clear desk and clear screen
|
|
12.2.1 Controls against malware
|
8.7 Protection against malware
|
|
12.7.1 Information systems audit controls
|
8.34 Protection of information systems during audit testing
|
|
13.1.1 Network controls
|
8.20 Networks security
|
|
13.1.3 Segregation in networks
|
8.22 Segregation of networks
|
|
14.2.1 Secure development policy
|
8.25 Secure development life cycle
|
|
14.2.5 Secure system engineering principles
|
8.27 Secure system architecture and engineering principles
|
|
14.3.1 Protection of test data
|
8.33 Test information
|
|
15.1.1 Information security policy for supplier relationships
|
5.19 Information security in supplier relationships
|
|
15.1.2 Addressing security within supplier agreements
|
5.20 Addressing information security within supplier agreements
|
|
15.1.3 Information and communication technology supply chain
|
5.21 Managing information security in the ICT supply chain
|
|
16.1.1 Responsibilities and procedures
|
5.24 Information security incident management planning and preparation
|
|
16.1.4 Assessment of and decision on information security events
|
5.25 Assessment and decision on information security events
|
|
17.2.1 Availability of information processing facilities
|
8.14 Redundancy of information processing facilities
|
|
18.1.4 Privacy and protection of personally identifiable information
|
5.34 Privacy and protection of PII
|
Merged controls:
| ISO/IEC 27002:2013 | ISO/IEC 27002:2022 |
|
5.1.1 Policies for information security
5.1.2 Review of the policies for information security
|
5.1 Policies for information security
|
|
6.1.5 Information security in project management
14.1.1 Information security requirements analysis and specification
|
5.8 Information security in project management
|
|
6.2.1 Mobile device policy
11.2.8 Unattended user equipment
|
8.1 User end-point devices
|
|
8.1.1 Inventory of assets
8.1.2 Ownership of assets
|
5.9 Inventory of information and other associated assets
|
|
8.1.3 Acceptable use of assets
8.2.3 Handling of assets
|
5.10 Acceptable use of information and other associated assets
|
|
8.3.1 Management of removable media
8.3.2 Disposal of media
8.3.3 Physical media transfer
11.2.5 Removal of assets
|
7.10 Storage media
|
|
9.1.1 Access control policy
9.1.2 Access to networks and network services
|
5.15 Access control
|
|
9.2.2 User access provisioning
9.2.5 Review of user access rights
9.2.6 Removal or adjustment of access rights
|
5.18 Access rights
|
|
9.2.4 Management of secret authentication information of users
9.3.1 Use of secret authentication information
9.4.3 Password management system
|
5.17 Authentication information
|
|
10.1.1 Policy on the use of cryptographic controls
10.1.2 Key management
|
8.24 Use of cryptography
|
|
11.1.2 Physical entry controls
11.1.6 Delivery and loading areas
|
7.2 Physical entry
|
|
12.1.2 Change management
14.2.2 System change control procedures 14.2.3 Technical review of applications after operating platform changes
14.2.4 Restrictions on changes to software packages
|
8.32 Change management
|
|
12.1.4 Separation of development, testing, and operational environments
14.2.6 Secure development environment
|
8.31 Separation of development, test, and production environments
|
|
12.4.1 Event logging
12.4.2 Protection of log information
12.4.3 Administrator and operator logs
|
8.15 Logging
|
|
12.5.1 Installation of software on operational systems
12.6.2 Restrictions on software installation
|
8.19 Installation of software on operational systems
|
|
12.6.1 Management of technical vulnerabilities
18.2.3 Technical compliance review
|
8.8 Management of technical vulnerabilities
|
|
13.2.1 Information transfer policies and procedures
13.2.2 Agreements on information transfer 13.2.3 Electronic messaging
|
5.14 Information transfer
|
|
14.1.2 Securing application services on public networks
14.1.3 Protecting application services transactions
|
8.26 Application security requirements
|
|
14.2.8 System security testing
14.2.9 System acceptance testing
|
8.29 Security testing in development and acceptance
|
|
15.2.1 Monitoring and review of supplier services
15.2.2 Managing changes to supplier services
|
5.22 Monitoring, review and change management of supplier services
|
|
16.1.2 Reporting information security events 16.1.3 Reporting information security weaknesses
|
6.8 Information security event reporting
|
|
17.1.1 Planning information security continuity
17.1.2 Implementing information security continuity
17.1.3 Verify, review, and evaluate information security continuity
|
5.29 Information security during disruption
|
|
18.1.1 Identification of applicable legislation and contractual requirements
18.1.5 Regulation of cryptographic controls
|
5.31 Legal, statutory, regulatory, and contractual requirements
|
|
18.2.2 Compliance with security policies and standards
18.2.3 Technical compliance review
|
5.36 Conformance with policies, rules, and standards for information security
|
Now that the two standards have been updated, the transition to ISO 27001:2022, which is the certifiable standard, must be completed before October 31, 2025.
That is why it is advisable to start working now on the new ISO/IEC 27002 controls, for example:
Get in touch with us today to learn how we can help you transition to ISO/IEC 27001 and 27002, 2022 versions.
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
I'm a senior cybersecurity and IT risks consultant with experience in design, implementation, and management of IT projects. Experience in audits and compliance consulting on ISO 27001, PCI DSS, and GDPR. More than fifteen years of experience in Cybersecurity and IT Risks, working in technical and sales areas with channel partners and value-added distributors. Relationship with vendors, channel partners, and end customers.
Comments