Athletics is considered to be the oldest sport in the world. Success is usually determined by one of two options: overcoming the opponent by speed (running as fast as possible a certain distance) and overcoming by endurance or depth (running a greater distance). When an athlete prepares for a competition, he must learn to manage these two variables very well: speed and endurance. If he runs too fast, his endurance will soon be exhausted. If he runs very slowly, his endurance will be better but his speed will be affected.
Athletic training consists of strategically combining speed and endurance in such a way that the increase in one does not affect the performance of the other. Both variables should increase in parallel.
Combining speed and endurance in cybersecurity
The same concept applies to the field of cybersecurity. If the objective is to achieve compliance and maintain managed risk levels, the vast majority of companies will tend to opt only for speed (implementing their controls quickly to achieve compliance). But this affects the maintenance of these controls over time (costs, personnel, time, etc.), decreasing their efficiency and effectiveness. Others, on the other hand, choose to implement their controls in a more staggered way (resistance), but they usually take so long that when they are ready, the threats have changed and the controls are no longer optimal.
The PCI Council has released "Best Practices for Maintaining PCI DSS Compliance". Here, they list a series of key strategies for maintaining speed in implementing controls along with resilience in the maintenance and management over time. The aim is to achieve strong and competitive risk-based compliance. Here is our analysis of the PCI Council’s supplement:
Why is a best-practice document necessary for maintaining PCI DSS compliance?
PCI DSS is a standard where compliance requires an annual report, either through a Self-Assessment Questionnaire (SAQ) or through a face-to-face audit by a Qualified Security Assessor (QSA). These periodic assessments tend to become a very important temporary milestone for those organizations affected. Depending on how the organization assumes this milestone, they may be susceptible to suffer from one of the most common errors in security: working solely on the basis of obtaining compliance, forgetting that security, in general terms, is an element that degrades over time.
The following figure explains this situation in an interesting way: If we look closely at the compliance curve, we see that it increases just before the arrival of the annual review. It decreases as this milestone passes, leaving the organization exposed to a sense of "false security" throughout the remaining time:
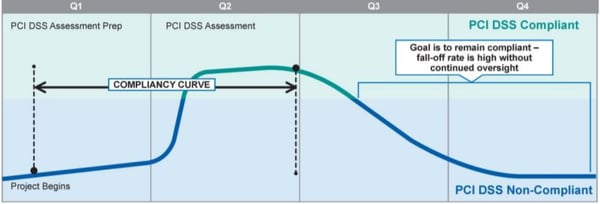 Figure 1. PCI DSS Compliance Curve (Source: PCI SSC)
Figure 1. PCI DSS Compliance Curve (Source: PCI SSC)
The PCI SSC through its Special Interest Group (SIG) analyzed this issue in 2018 and in January 2019 published an updated version of the information supplement “Best Practices for Maintaining PCI DSS Compliance”. The main objective of the supplement is to change the “only compliance” mentality to one focused on the continuous management of risk over time.
What are the PCI Council's key recommendations for optimal management of PCI DSS compliance maintenance?
Based on the results of Verizon's 2017 Payment Security Report, more than 44 percent of the organizations included in the study have seen the effectiveness of their PCI DSS controls and their overall compliance status decrease right after the annual assessment is completed. This was due to organizational changes, overconfidence in the controls deployed, drawbacks in the selection of people, tools and processes, lack of leadership and management support, and problems in identifying the Cardholder Data Environment (CDE).
In light of this, the document outlines 10 recommendations to establish a framework for the adaptation and improvement of security controls within an organization's usual activities. It should be noted that the purpose of these recommendations is not to replace or extend the scope of the PCI DSS requirements:

1. Develop and maintain a sustainable security program, focusing efforts on payment card data security beyond simple regulatory compliance. The identification of processed, stored and/or transmitted payment card data and the elimination of this information when it is no longer required are key to optimizing protection actions.
2. Develop program, policy and procedures that establish objectives, roles and responsibilities, as well as the rules to be followed and the tasks that accompany them. This regulatory framework must be known by all internal employees, contractors, suppliers, etc. linked to the cardholder's data environment.
3. Develop performance metrics to measure success, or, as management philosopher Peter Drucker put it, "If you can’t measure it, you can’t improve it". A metric allows us to know the state of a particular control at a specific moment, allowing us to check whether that state is within acceptable thresholds. The establishment and periodic collection of metrics allow the organization to identify compliance deviations and correct errors before they are magnified. For example, for PCI DSS requirement 6.2 (update management) a metric that could be applied would be to measure the percentage of known vulnerabilities whose updates have been applied or mitigated over a period of time (monthly, for example).
4. Assign ownership for coordinating security activities, ensuring that each action has an associated role and there is support from the management. This involves the use of specific tools, economic budgets, resources, knowledge of the organization and security issues, etc. Also, emphasis is placed on a special role: The Compliance Manager - the person in charge of coordinating the correct development of all tasks and the gathering of evidence to demonstrate that the execution of controls is effective over time.
In order to facilitate the identification of roles involved in compliance management tasks, the document includes a special annex (Annex B: "Common Assessment Roles and Responsibilities"), with an illustrative table of different groups/roles and their common tasks.
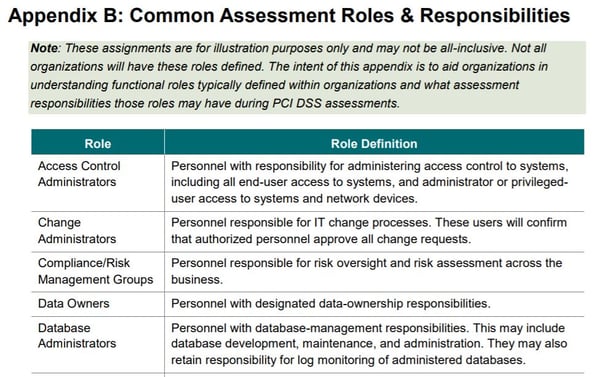 Figure 2. Matrix of assignment of roles and responsibilities (Source: PCI SSC)
Figure 2. Matrix of assignment of roles and responsibilities (Source: PCI SSC)
5. Emphasize security and risk management to attain and maintain compliance, as compliance by itself does not involve proper safety. A more effective approach is to focus on creating a culture of security and protecting an organization's information assets and IT infrastructure and enabling compliance to be achieved as a direct result of these actions. How can this be achieved? Through the periodic execution of a risk analysis, which will allow the early identification of risks (in the case of security breaches, implementation of new technologies or significant changes, etc.) and the generation of actions aimed at managing it and alignment with other security frameworks such as the ISO 27000 series, COBIT, etc. More information can be found in the PCI DSS Risk Assessment Guidelines Information Supplement, also published by the PCI SSC.
6. Continuously monitor security controls to verify that processes are aligned with the organization's business and security objectives. To this end, a series of actions are recommended:
a) Review of the scope of compliance,
b) Review of compensatory controls,
c) Use of automated monitoring of controls; and
d) Use of manual revisions
All within a pre-established frequency and sampling.
7. Detect and respond to security control failures as a direct response to obtaining information on the status of security controls if these results are found to be outside optimal thresholds. This requires assigning responsibility for detection and response to a specific team or individual, establishing controls to detect security breaches, restoring the security of the environment if an incident occurs, identifying the causes of control failures, identifying potential new problems, and implementing failure mitigation measures.
8. Maintain security awareness through periodic employee training campaigns and establishing effective communication channels for the distribution of policies and procedures. The thematic content of these campaigns must be constantly updated and adapted to the latest environmental threats and risks.
9. Monitoring compliance of third-party service providers since, being part of the compliance environment, they can become a risk vector if their own policies are not aligned with the organization's security objectives. Monitoring your compliance status, determining responsibilities, and responding to any contractual changes are part of the service provider management strategy, as outlined in the PCI SSC Third-Party Security Assurance Information Supplement.
10. Evolve the compliance program to address changes in the security program, organizational, operational environment, and scheduled technology retirement. Only in this way can you have a dynamic program avoiding stagnation and misalignment with the "real" operating environment. As an example, in annex C "Applicability of PCI DSS Requirements to Assets Type" a very interesting example table is presented that relates each asset in the environment with the PCI DSS requirements applied to it and its responsible party:
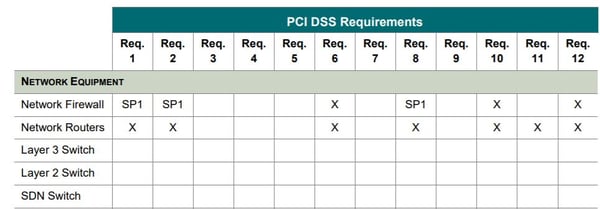 Figure 3. Table of Applicability of PCI DSS Requirements to Assets Type (Source: PCI SSC)
Figure 3. Table of Applicability of PCI DSS Requirements to Assets Type (Source: PCI SSC)
Finally, Annex D of this information supplement lists a series of activities to be included in the PCI DSS compliance program, which can serve as a baseline for the identification of activities that must be validated within certain intervals. Obviously, these recommendations must be adjusted to each entity according to its needs:

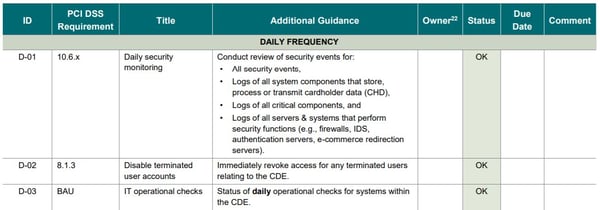 Figure 4. Extract from the PCI DSS Compliance Program Activities Table (Source: PCI SSC)
Figure 4. Extract from the PCI DSS Compliance Program Activities Table (Source: PCI SSC)
Final thought
The first version of the information supplement “Best Practices for Maintaining PCI DSS Compliance” was published in August 2014. The newly restructured version brings new recommendations to organizations that must comply with PCI DSS can maintain the standard’s security controls over time. The goal is to make organizations aware that regulatory compliance is not synonymous with security. Multiple activities are required over time to keep risk levels below acceptable thresholds for the organization, beyond simply receiving a certificate of approval or third-party compliance.
.png)




















Comments