Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

Social engineering is the attempt, by malicious individuals to gain information, access, or introduce unauthorized software into an organization's environment through the manipulation of end-users.
Social engineering is fast becoming one of the primary attack techniques that hackers use to exploit a weakness in an organization. PCI DSS requires that a penetration test considers the threats and vulnerabilities experienced by organizations in the last 12 months, which may include social-engineering attacks. For example, social engineering may be used as a method used for introducing malware into the environment.
Social-engineering tests are an effective method of identifying risks associated with a lack of security awareness of end-users. Any social engineering tests performed will be appropriate for the size and complexity of the organization and should consider the maturity of the organization’s security awareness program. These tests may include in-person, non-technological interactions, such as persuading someone to hold open a door or remote interactions such as having someone provide or reset a password or convincing the end-user to open a vulnerable e-mail attachment or hyperlink.
But how do social engineering attacks work in real life?
Social engineering attacks, like other attacks and genuine ethical penetration testing, follow a defined lifecycle methodology. The steps are clear and defined but there are different ways to approach each target.
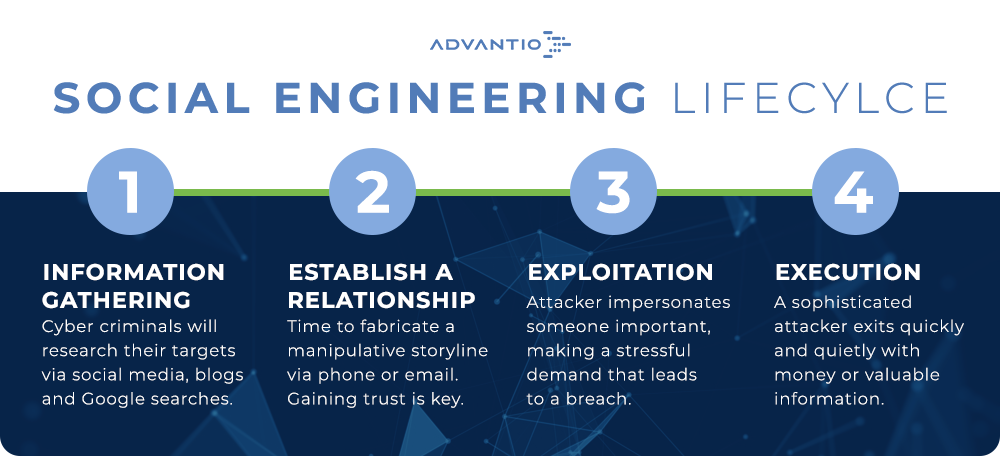 1.Information Gathering: Gathering as much information on the target as possible through the use of Open Source Intelligence Techniques (OSINT)
1.Information Gathering: Gathering as much information on the target as possible through the use of Open Source Intelligence Techniques (OSINT)
2. Establish Relationship: Engaging the target though targeted communications such as social media or emails.
3. Exploitation: Uses Information and relationship to gain a ‘foothold’ i.e. giving away sensitive information or holding the door open for a ‘familiar’ face
4. Attack Execution: perform the attack, erasing the digital footprint and exiting from the attack before any alarm can be raised.
This stage of an attack is often the longest and requires the attacker to gather information about the target, either an organization or person usually. To do this the attacker exploits Open Source Intelligence Gathering Techniques (OSINT) such as researching the targets social media accounts and networks, websites, and blogs, Google searches on individuals, associated people and companies. Attackers use can use this information to impersonate individuals within the target's network or to gain a sense of familiarity with the target. For example, an attacker may use information published on a website or social media platform such as LinkedIn to pretend to be a third party in a project that the victim's company is promoting to gain trust with the victim hoping they will reveal sensitive information. Remember to be aware of the information and audience you are publishing online to.
Attackers focus on creating a good fabricated scenario where they can manipulate and steal their victims’ personal information. They do this by establishing a trusting relationship with the target to put them in a relaxed and comfortable state where it is easier to gain useful or sensitive information.
The true art of social engineering is to elicit information from the victim without directly asking for it. This technique can be used via voice or email, using different types of questions and techniques to passively force the victims into revealing sensitive information.
To avoid falling victim to this type of technique it is always important to double-check the identity of the person your speaking to and don’t be afraid of saying no if you think something isn’t right or someone is asking for sensitive information.
Exploitation happens when the attacker uses the information they have gathered and the relationship they have established to actively gain access or infiltrate the target. Most targeted groups are Junior Staff, Administrators, Support Staff. They can be easily manipulated through the simulation of requests impersonating a “higher position” person in the company. Sometimes attackers knowingly place target persons under an imposed time constraint, such as completion of a contract or payment of an invoice, to put them under pressure forcing a decision under stress. Under this pressure, individuals can make mistakes and an attacker can force a change of account details on a payment or get an individual to disclose sensitive information such as passwords and usernames.
This is the attack phase of social engineering, when a social engineer realizes their end goal, often walking away with sensitive information or money. A sophisticated attacker will reduce their digital footprint and exit the attack quietly and smoothly giving them the maximum amount of time before the attacks have been noticed.
Big organizations spend a lot of time, money and effort securing the technical infrastructure of an organization but often fail to remediate the biggest vulnerability in their organization which is people. The video below excellently demonstrates just how effective a social engineering attack can be. The attacker is performing a classic ‘con’ creating a false sense of pressure to manipulate the victim into surrendering information.
Remember organizational policies and procedures are there to ensure that individuals can’t circumnavigate the system. If you are unsure always escalate the issue, and if you are responsible for staff who deal with the public and third parties ensure that they are well trained and always feel comfortable challenging nonstandard practices and raising issues and potential fraudulent activity to appropriate individuals. Don’t let you or your organization fall foul of the thousands of social engineering attacks that happen each year.
If you have engaged a cyber security consultancy firm, like Advantio, to perform a social engineering test with your organization you must be provided with details of the activity they took an in-depth report and results.
A detailed report will allow your organization to examine the vulnerabilities in your defenses against social engineering attacks and plan improvement, whether they are technical (better email filtering) or training and education (letting people know how to spot potential attacks).
A business needs to be updated on the latest social engineering attacks and tools hackers use to manipulate individuals. Employees must be empowered to check the authenticity of a person or a request. There must be defined security flows to follow, where double checks are in place and data is stored and reachable by only those who need to know.
A well-detailed report also helps organizations to update their internal security awareness and training, ensuring that it stays current and engages employees at the right levels across the business. Social engineering is one of the biggest cyber threats facing organizations. Figures published by the FBI in the past two years help us better understand the potential cost business are facing from a breach.
"Social engineering attacks can be quantified in $1.6 billion from 2013 to 2017.
130 security breaches every year, companies pay an average cost of $11.7 million for it.
“Federal Bureau of Investigation”
In the age of cybercrime, hackers will use any means necessary to leverage an advantage over their targets. As organizations' technical security defense becomes more sophisticated hackers target the weakness link in the security chain, non-security aware individuals.
The best way to tackle this threat is to engage a specialist consultancy firm, understand the social engineering assessments and plan a targeted organization-wide awareness and education campaign. To understand how this applies to your industry please contact us.
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
Security Consultant with more than 8 years of experience within the cyber security and IT. I’ve been involved in PCI CPP project for a global payment service provider, lead several SOC departments and now performing Ethical Hacking activities.
Comments