Because of the COVID-19 epidemic, the company's employees, contractors, business partners, vendors, and other roles involved in PCI DSS activities have had to change the way they connect to the Cardholder Data Environment (CDE) to do their job. Many of these connections are now made remotely, using employees' home connections and - in some cases - using non-corporate computers, exposing the organization to attack vectors that did not exist when these connections were made locally.
This situation has forced many companies to implement their continuity plans to ensure that operation continues under this exceptional scenario, testing the requirement 12.10 of PCI DSS, which requires the existence of an incident response plan that incorporates business recovery and continuity actions.
This article will list the PCI DSS controls that apply to all remote connections to the CDE, based on the following generic network architecture. It will help to minimize the risk these connections bring to the Cardholder Data Environment, avoid amplification of the compliance environment, and ensure that remote connections meet PCI DSS criteria:
- A network segment that contains the assets that process, store and/or transmit payment card data (Cardholder Data Environment - CDE) - Fully in scope for all applicable PCI DSS requirements.
- A network segment that contains several assets that are connected or may impact the security of the CDE, including a jump server (jump box/bastion host) - Fully in scope for all applicable PCI DSS requirements.
- A home network (untrust), which includes a workstation with administrative access to the cardholder data environment. This workstation is entirely in scope for all applicable PCI DSS requirements.
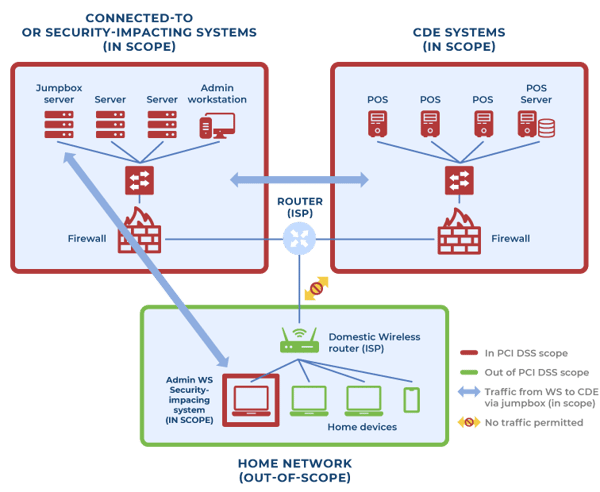
It is assumed that the platform that enables remote connections (virtual private network connections (IPSEC/TLS VPN), virtual desktop infrastructure (VDI), remote desktop services (RDS), etc.) and the workstation connecting to the environment remotely is compliant with PCI DSS controls while in the compliance environment (In scope).1
The PCI DSS requirements that are exclusively applicable to workstations that connect remotely to the CDE are:
PCI DSS Requirement
1.4
Security Control:
Personal Firewall
Description
Install personal firewall software or equivalent functionality on any portable computing devices (including company and/or employee-owned) that connect to the Internet when outside the network (for example, laptops used by employees), and which are also used to access the CDE. Firewall (or equivalent) configurations include:
- Specific configuration settings are defined.
- A personal firewall (or equivalent functionality) is actively running.
- A personal firewall (or equivalent functionality) is not alterable by users of portable computing devices.
PCI DSS Requirement
8.1.5
Security Control:
Third-part remote access
Description
Manage IDs used by third parties to access, support, or maintain system components via remote access as follows:
- Enabled only during the period needed and disabled when not in use.
- Monitored when in use.
PCI DSS Requirement
8.3.2
Security Control:
Multi-factor authentication (MFA) controls
Description
Incorporate multi-factor authentication for all remote network access (both user and administrator, and including third-party access for support or maintenance) originating from outside the entity's network.
PCI DSS Requirement
8.5.1
Security Control:
Use of unique credentials by each customer (only applicable to service providers)
Description
Service providers with remote access to customer premises (for example, for support of POS systems or servers) must use a unique authentication credential (such as a password/phrase) for each customer.
PCI DSS Requirement
12.3
Security Control:
Usage policies for critical technologies (including remote access)
Description
Develop usage policies for critical technologies and define proper use of these technologies, including:
- Explicit approval by authorized parties
- Authentication for the use of the technology
- A list of all such devices and personnel with access
- A method to accurately and readily determine owner, contact information, and purpose
- Acceptable uses of the technology
- Acceptable network locations for the technologies
- List of company-approved products
PCI DSS Requirement
12.3.8
Security Control:
Automatic disconnection of remote access sessions
Description
The automatic disconnect of sessions for remote-access technologies after a specific period of inactivity
PCI DSS Requirement
12.3.9
Security Control:
Use of remote access for third parties only when necessary
Description
Activation of remote-access technologies for vendors and business partners only when needed by vendors and business partners, with immediate deactivation after its usage.
PCI DSS Requirement
12.3.10
Security Control:
No copying, moving or storing of card data when accessed remotely
Description
For personnel accessing cardholder data via remote-access technologies, prohibit the copying, moving, and storage of cardholder data onto local hard drives and removable electronic media unless explicitly authorized for a defined business need. Where there is an authorized business need, the usage policies must require the data to be protected per all applicable PCI DSS Requirements. .
However, additional security controls beyond PCI DSS can be deployed to improve the security levels of the remote workstation, such as Data Loss Prevention (DLP), Host DS/IPS, USB and removable device media management, and other threat defense tools, based on company's security strategy.
Besides, the PCI Security Standards Council (PCI SSC) has published the following documents to help merchants and service providers maintain the same levels of local (onsite) security on remote connections:
Finally, other organizations also have available material that may be useful in protecting teleworking connections or remote access:
As experienced security professionals, Advantio has the necessary expertise to help better secure your network.


.png)

















Comments