Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.
Visa Europe revealed important stats about the usage of Contactless Cards. Poland, Spain and the UK use this payment methd the most, with UK usage growing by 300% year over year.

OWASP describes itself as:
"The OWASP Testing Project has been in development for many years. The project aims to help people understand the what, why, when, where, and how of testing web applications".
But for us, it is also an essential guide, point of reference, and a mentality that we use every day to help our customers to grow in the security field and a must to follow for every testing activity.
The test action is used to identify and evaluate the solidity of the applications and the infrastructure it hosts, concerning the increasingly known, unknown, and not always mitigable vulnerabilities.
The OWASP, in this case, helps us with a lot of useful information on what to check and what significant vulnerabilities are present in all applications. It also provides guidance and is a great reference point for managing applications.
The activity is a continuous process over time, that is: before writing the code (design and manual review) while writing the code (code review) and after its publication (Penetration Test and VA).
When offering services exposed to the public (Internet), it is good practice to periodically carry out checks to make sure that your applications are not vulnerable.
Internal testing is also essential, as many of the attacks can come from the second line, where it is thought to be safer behind well-configured firewalls. They, once bypassed, expose all services and applications to high risks. If not configured/developed correctly, they can be six succulent targets for attackers.
The OWASP suggests us to implement, if you have not already done so, the following scheme for your applications called Software Development Life Cycle (SDLC):
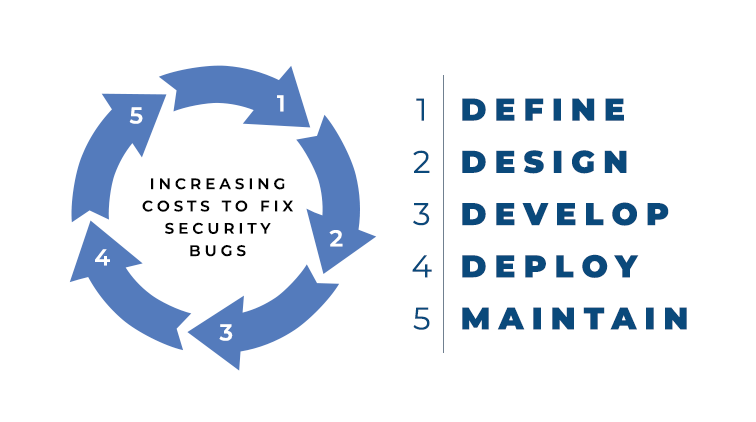 OWASP suggests that we define the project with all its risks, costs, timescales, and functionality. Once the plan has been determined, we move on to studying the design of the application. After the second step, you can move on to the actual development and then to its publication. But it does not end there; the maintenance of your application is of fundamental importance and must be a continuous activity over time. The life cycle is repeated in the same way that each change or a new application is developed to improve the environment continuously.
OWASP suggests that we define the project with all its risks, costs, timescales, and functionality. Once the plan has been determined, we move on to studying the design of the application. After the second step, you can move on to the actual development and then to its publication. But it does not end there; the maintenance of your application is of fundamental importance and must be a continuous activity over time. The life cycle is repeated in the same way that each change or a new application is developed to improve the environment continuously.
The areas affected by this activity are not only technological ones. Below the OWASP suggests the following points that should always be tested:
People – to ensure that there are adequate education and awareness;
Process – to ensure that there are adequate policies and standards and that people know how to follow these policies;
Technology – to ensure that the process has been effective in its implementation.
Every step is essential because if you fail in one of the points, you leave an open door for the attacker to compromise your environment.
Cyber security awareness courses for your employees are a vital point because they have to know how to use the technology adopted in the company properly.
Processes are essential for people. If people have high skills and sound knowledge, but the rules and policies are written in the wrong way, there could be a gap in security. It could allow an attacker to exploit the process and gain sensitive information useful for future attacks. A fair process should also contain possible exceptions.
If the technology is not adequate for the application you want to develop, you will always be a step behind the attackers. You will need a technology that is common in life and continuously updated and fixed from the newly discovered vulnerabilities.
To perform the testing properly, you need to use the right tools. Hence you need qualified employees who know how to use the proper testing techniques.
OWAS suggests the following methods for manual testing:
In many cases, it is essential to use automatic scans. They help to carry out the work of humans as they can test large quantities of vulnerabilities quickly. But scans are not the right tool if not accompanied by manual testing. Automated tests often generate many false positives and do not always manage to exploit or find the vulnerabilities that lie right before their eyes.
The importance of manual testing is of fundamental significance as specialists can identify unknown vulnerabilities or exploit what the scan has found as a trivial threat and turn it into a real attack that will steal all your data.
For instance, in code review, you can use a tool that analyzes millions of code lines and finds many false positives. This data must be examined manually by the code reviewer to make sure that there is a flaw in the code.
But the code reviewers don't just stop to check the tool's output; they also manually analyze all the code they deem most sensitive. This is not controlled by the tool where the lines of code are of equal importance to it. The same thing happens for penetration testing activities where the ethical hacker has an open vision and experience that helps to exploit vulnerabilities that an automatic tool would not be able to do. In many cases, the attacks are carried out manually as each infrastructure and application is different and must be studied. The tools are handy for the penetration tester to identify and evaluate every single option that can be exploited when performing the attack. Still, they do not guarantee efficient control, such as the manual one.
The costs and timing do not play in favor of manual controls. Still, it must be remembered that the attackers have as much time as they want available, and a simple computer and a connection are enough to attack your applications.
Manual inspection and review of company processes and policies are of fundamental importance to prevent the possibility of being attacked.
OWASP is a point of reference for every person that works in the development and other fields impacted by cyber security. Their guidelines and mentality help people to understand the right way and steps to follow to have a secured application.
The OWASP recently released a new version of their guide: OWASP 4.1 (https://owasp.org/www-project-web-security-testing-guide/v41/). In this update, they focus on the importance of the manual testing and review process that in the last year is significantly underestimated.
They want to remind you that the right workflow, tools, testing activities, and good reports are essential to have an excellent overview of your application and what you need to develop it securely.
| Column Header Text | Column Header Text | Column Header Text |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
|
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Their work should have not stopped there because achieving compliance is an occasional result that doesn't ensure a continual protection. |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Performing a review of the media inventories at least annually |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
Row Header Text |
Lorem ipsum dolor sit |
Lorem ipsum dolor sit |
23 |
 Image caption goes here. This is HTML text.
Image caption goes here. This is HTML text.
Security Consultant with more than 8 years of experience within the cyber security and IT. I’ve been involved in PCI CPP project for a global payment service provider, lead several SOC departments and now performing Ethical Hacking activities.
Comments